6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Descrição
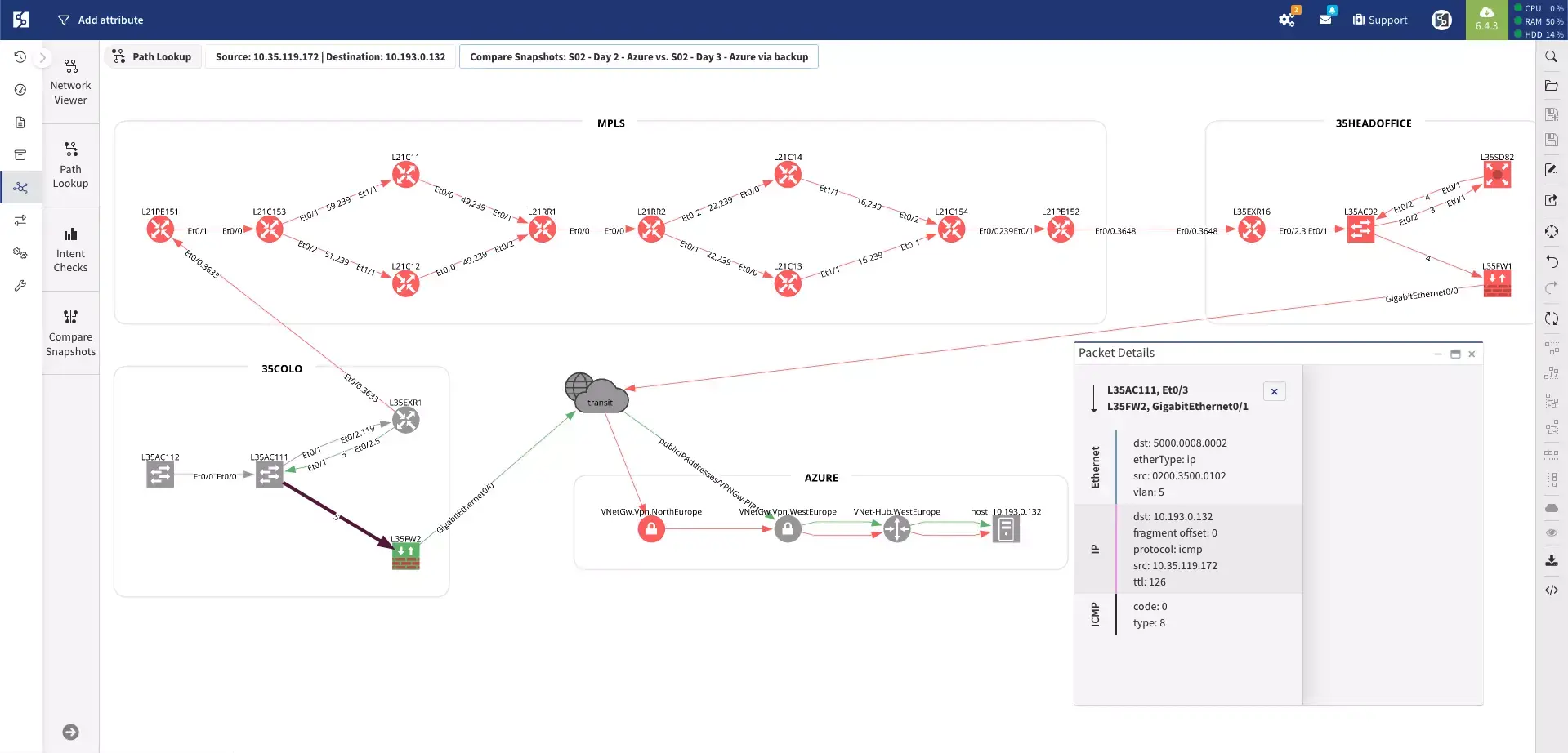
Network Security Assurance Network Security Audit with IP Fabric

The United Nations World Water Development Report 2023: partnerships and cooperation for water
KC has over 100 crypto ATMs, mostly in low-income neighborhoods
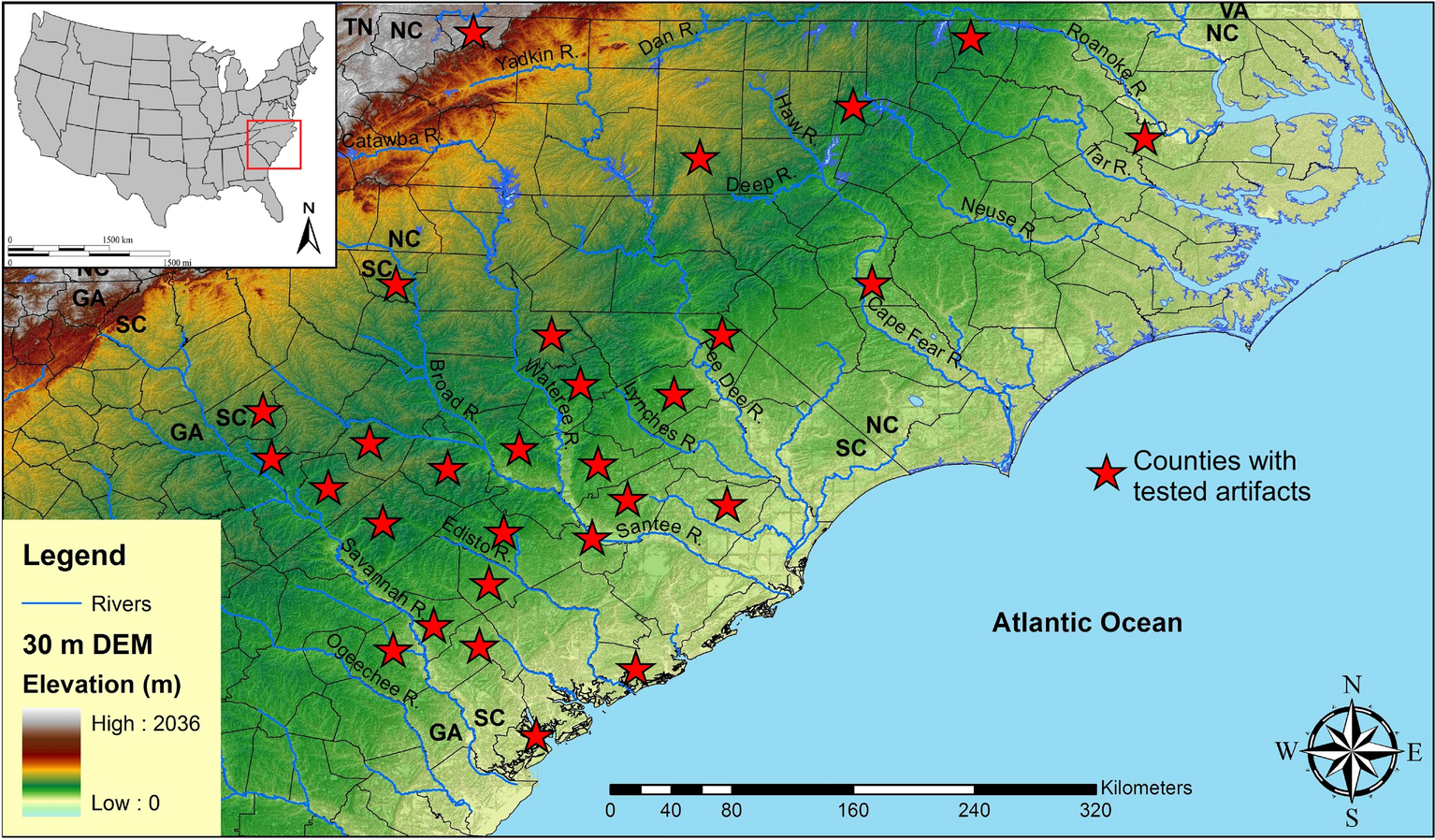
Paleoamerican exploitation of extinct megafauna revealed through immunological blood residue and microwear analysis, North and South Carolina, USA

Controlling a Chemical Coupling Reaction on a Surface: Tools and Strategies for On-Surface Synthesis

Experts released PoC exploit for MOVEit Transfer CVE-2023-34362

Windows 10 Nt Heap Exploitation (English version)

Experts released PoC exploit code for Cisco IOS XE flaw CVE-2023-20198
WordPress Security Plugin

Connecting the dots in trustworthy Artificial Intelligence: From AI principles, ethics, and key requirements to responsible AI systems and regulation - ScienceDirect

Computer security - Wikipedia
WordPress 6.4 Release Update - DreamHost

Evil_MinIO exploit used in attacks on MinIO Storage Systems
de
por adulto (o preço varia de acordo com o tamanho do grupo)