Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
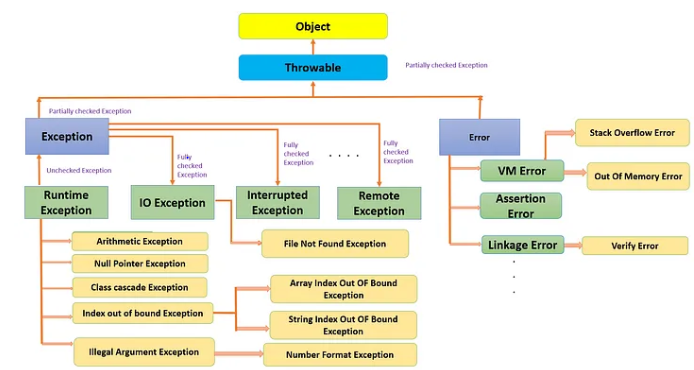
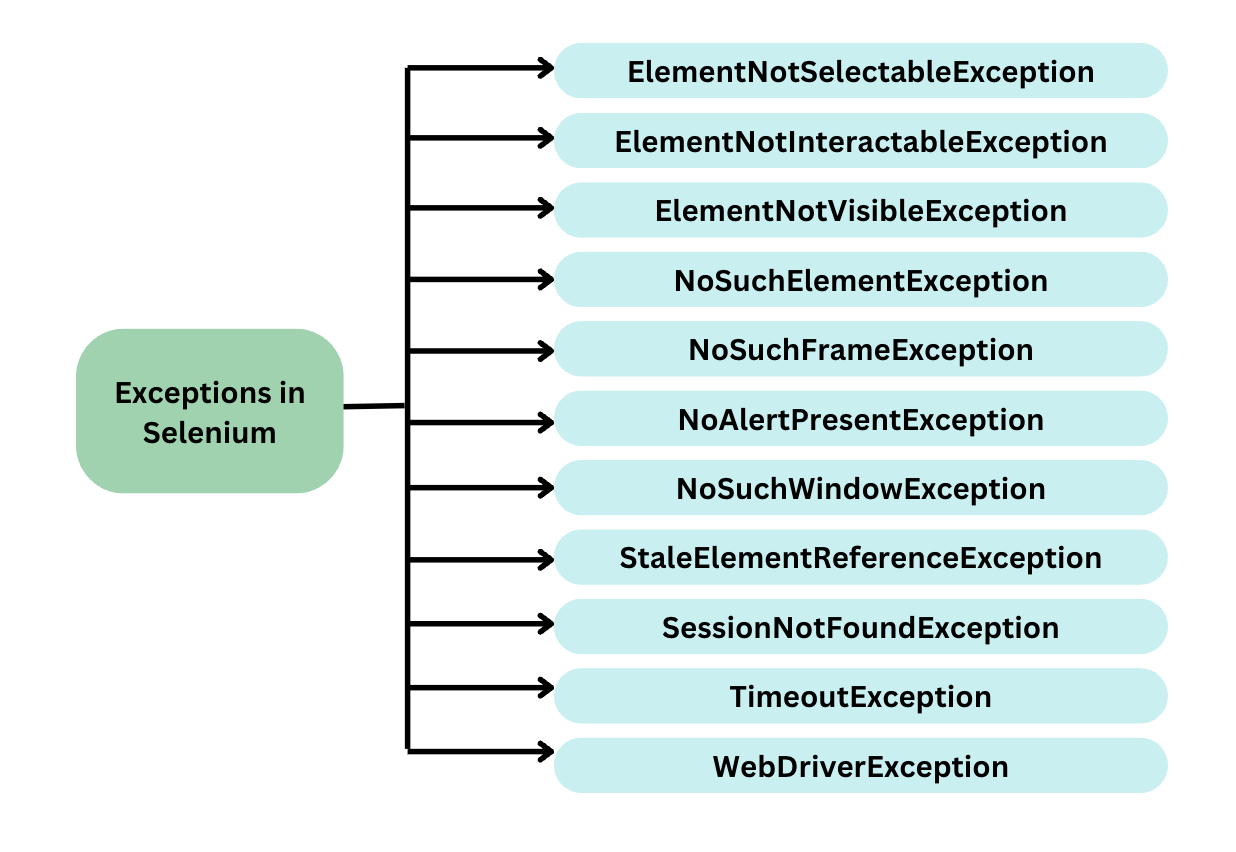
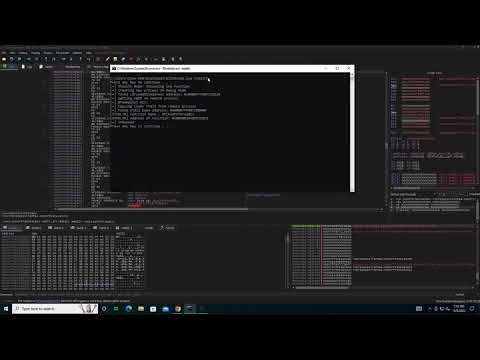
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.
Blindside: A New Technique for EDR Evasion with Hardware

Why Instagram Threads is a hotbed of risks for businesses
Abusing Exceptions for Code Execution, Part 2

Microsoft Defender Attack Surface Reduction recommendations

Changing Spring Boot Env Properties at Runtime
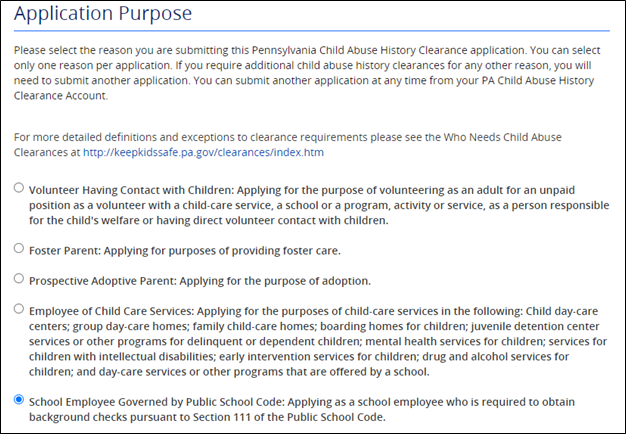
Instructions for Obtaining a Pennsylvania Child Abuse History

Secure Your AWS EC2 IMDS - Tenable Cloud Security
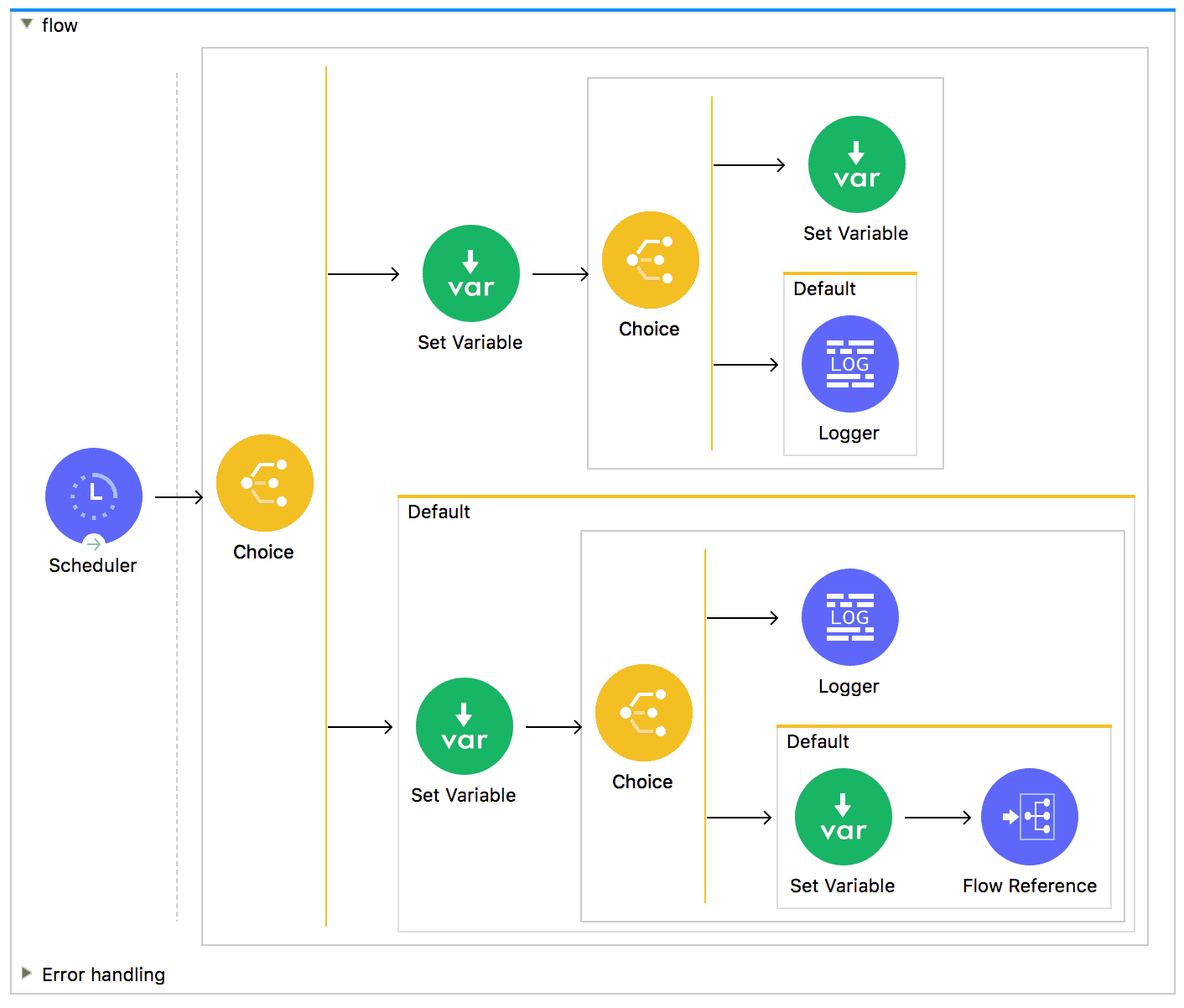
Mule programming style guide: stop abusing the choice router
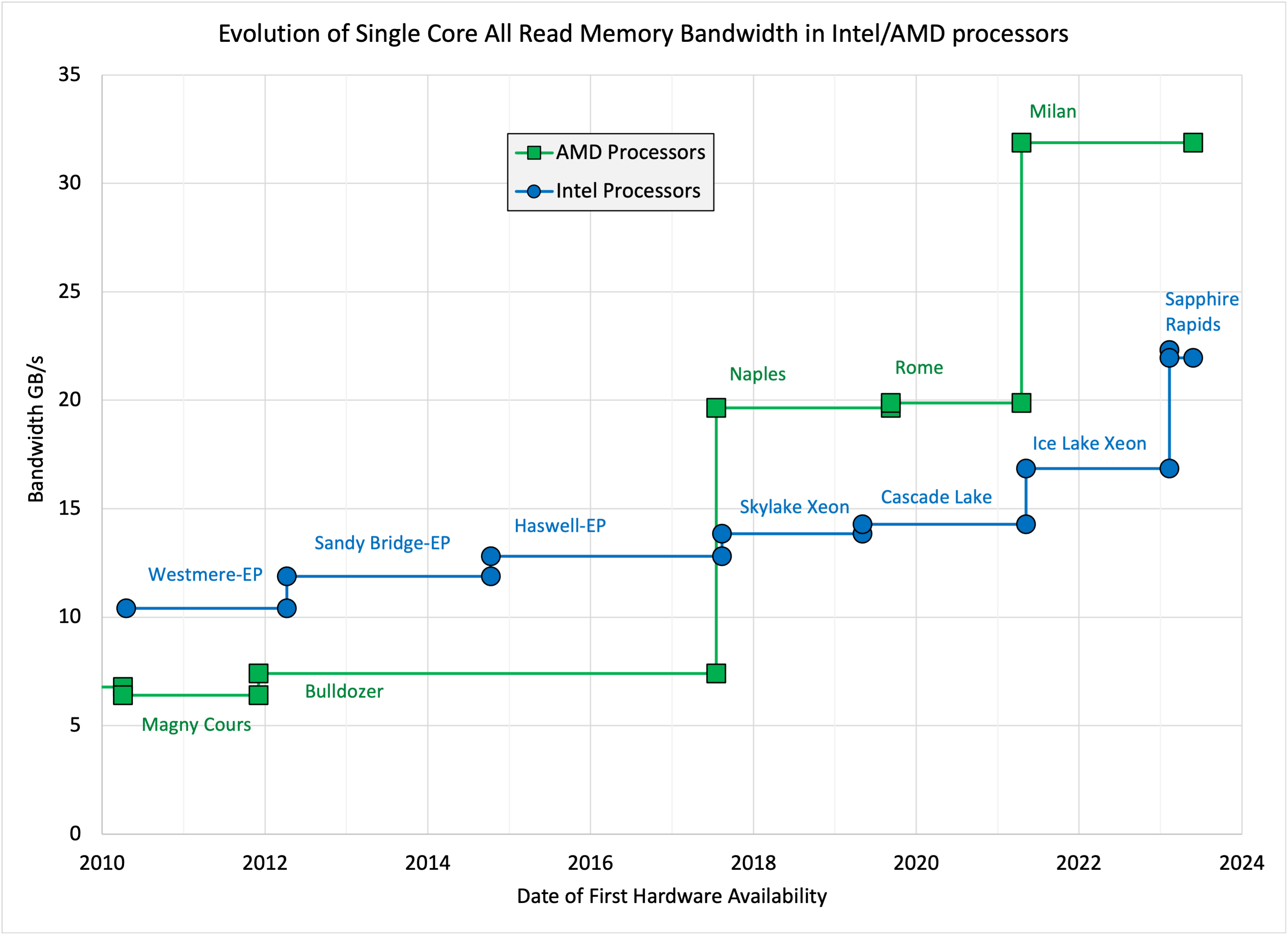
John McCalpin's blog » STREAM benchmark
Sample Terms of Use Template and Guide - Termly

exception processing message 0xc0000005 - unexpected parameters

IoT Security Exposed: Unveiling Azure Defender Flaws

What is an Integer Overflow Attack (with Examples)?
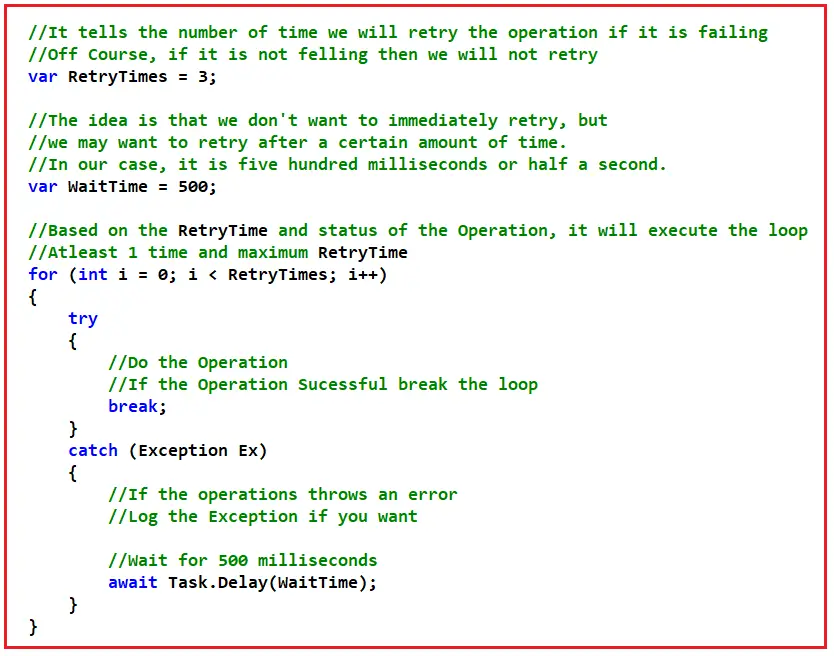
Retry Pattern in C# with Examples - Dot Net Tutorials
de
por adulto (o preço varia de acordo com o tamanho do grupo)