Complete UAF exploit - UD Capture
Por um escritor misterioso
Descrição

Exploiting a textbook use-after-free in Chrome

Firefox Referrer-Policy: Use-after-free vulnerability

Automated Use-After-Free Detection and Exploit Mitigation: How Far
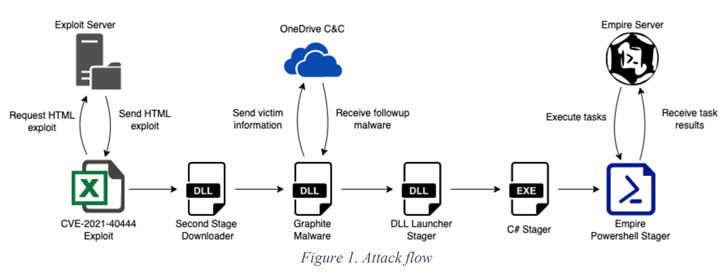
Hackers Exploited MSHTML Flaw to Spy on Government and Defen

Automated Use-After-Free Detection and Exploit Mitigation: How Far

CVE-2018-8611 Exploiting Windows KTM Part 4/5 – From race win to
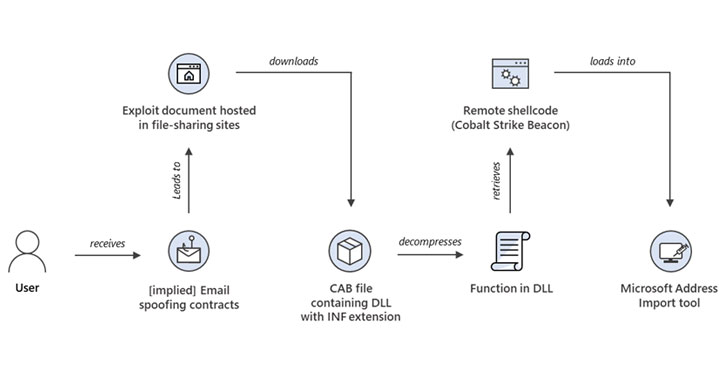
Windows MSHTML 0-Day Exploited to Deploy Cobalt Strike Beaco
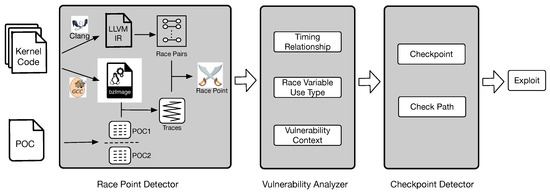
Applied Sciences, Free Full-Text

A fine-grained classification and security analysis of web-based

UAF-GUARD: Defending the use-after-free exploits via fine-grained

Released! PS5 Kernel exploit + Webkit vulnerability for Firmware

Top Russian General Possibly Captured in UAF Kharkiv Offensive

Pwnable-Sherpa: An interactive coaching system with a case study
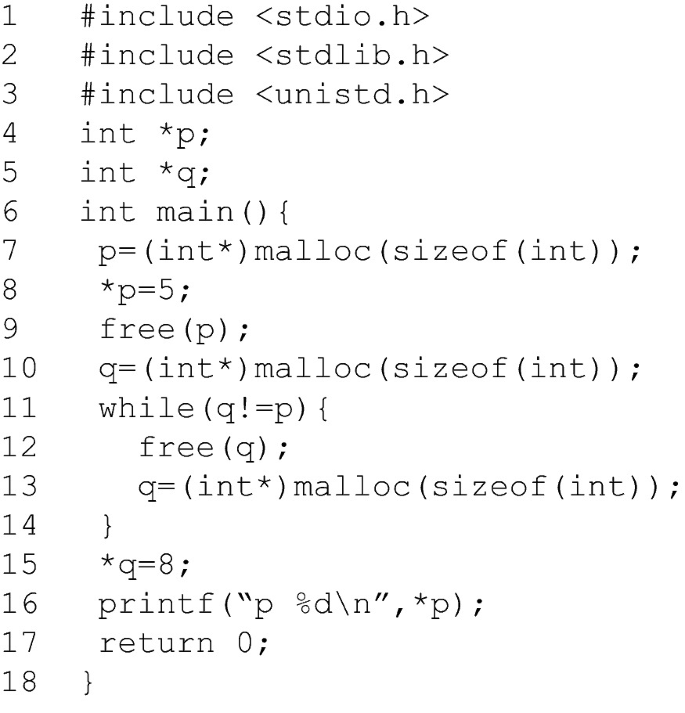
A Survey of Detection Methods for Software Use-After-Free

CVE-2021-31956 Exploiting the Windows Kernel (NTFS with WNF
de
por adulto (o preço varia de acordo com o tamanho do grupo)




/cdn.vox-cdn.com/uploads/chorus_asset/file/24400151/RISING_STAR_2.jpeg)

