Anti-Exfil: Stopping Key Exfiltration, by Blockstream, Blockstream Engineering Blog
Por um escritor misterioso
Descrição
In the wake of our recent launch of Blockstream Jade, we’d like to talk about a feature we’ve developed to eliminate the possibility of a certain hypothetical undetectable attack that a hardware…

Blockstream

Blog - Block Key Capital - Research

Advanced EXE Multi Protection Against Reverse Engineering with

Blockstream
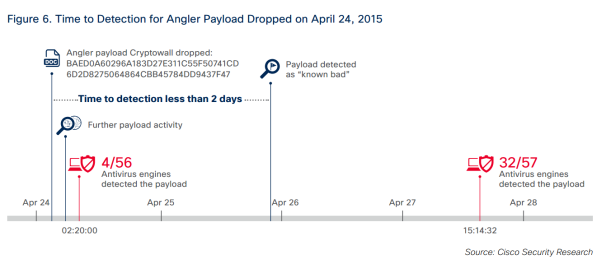
The Ultimate Guide to Angler Exploit Kit for Non-Technical People
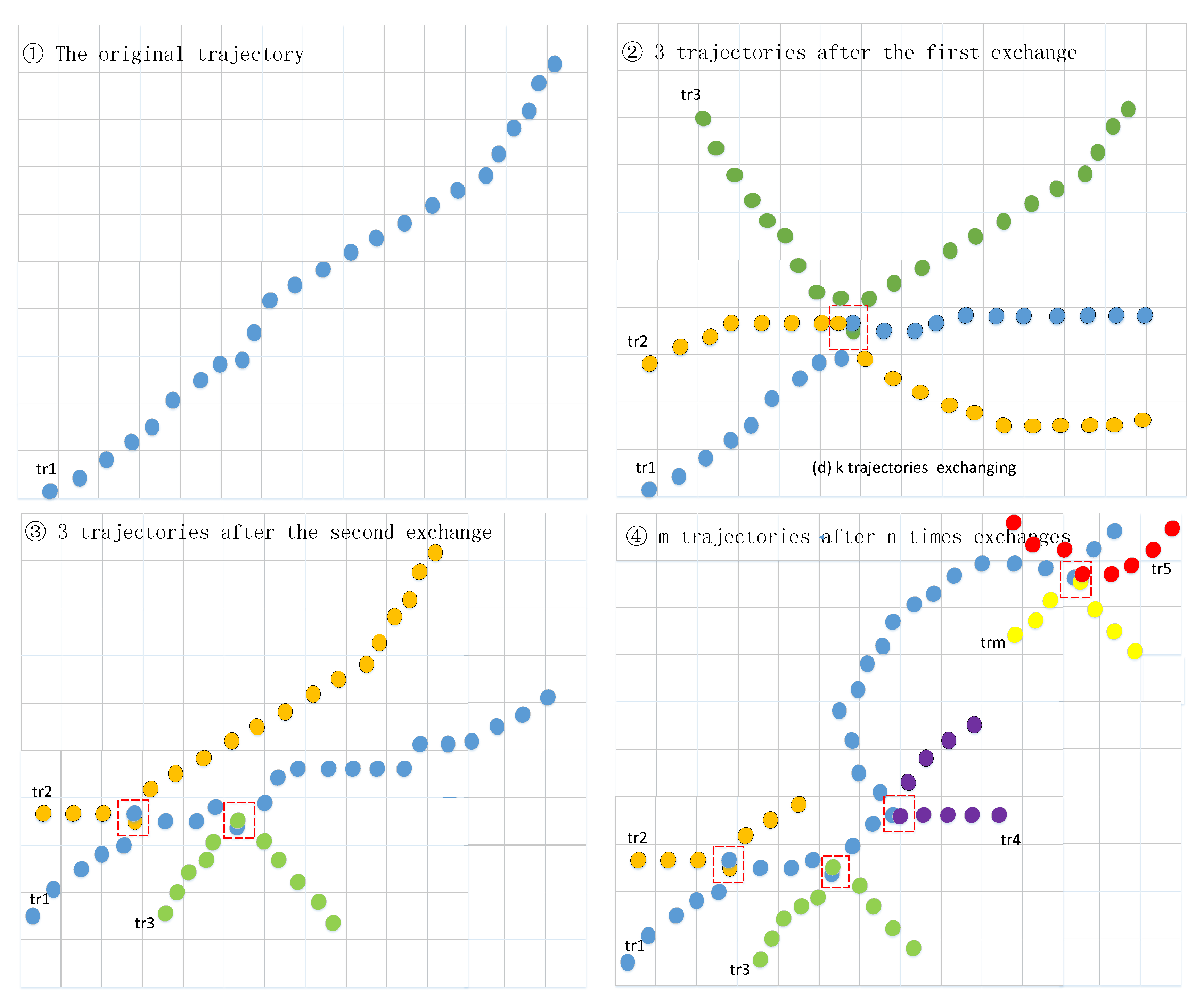
IJGI, Free Full-Text
sec_profile/README_2016.md at master · tanjiti/sec_profile · GitHub

Blockstream Users Targeted by Phishing Email
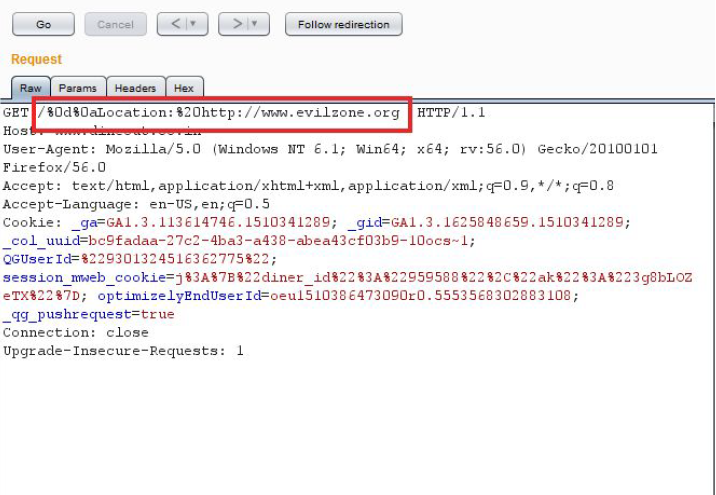
BugBounty — Exploiting CRLF Injection can lands into a nice bounty
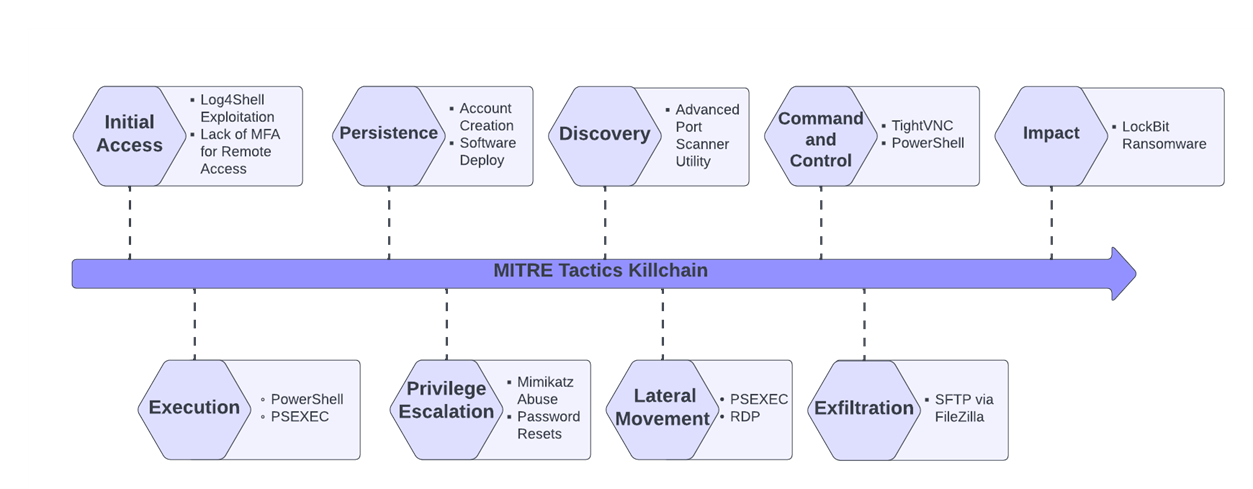
Anatomy of a LockBit Ransomware Attack
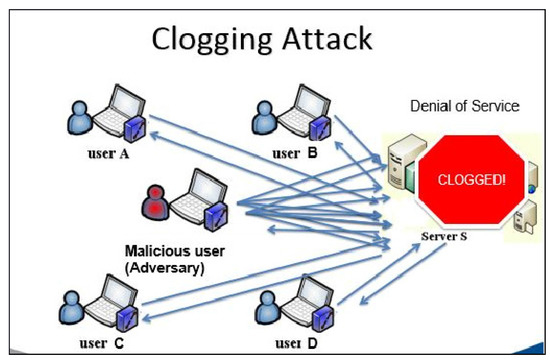
Cryptography, Free Full-Text

How behavioral blocking & containment stops post-exploitation
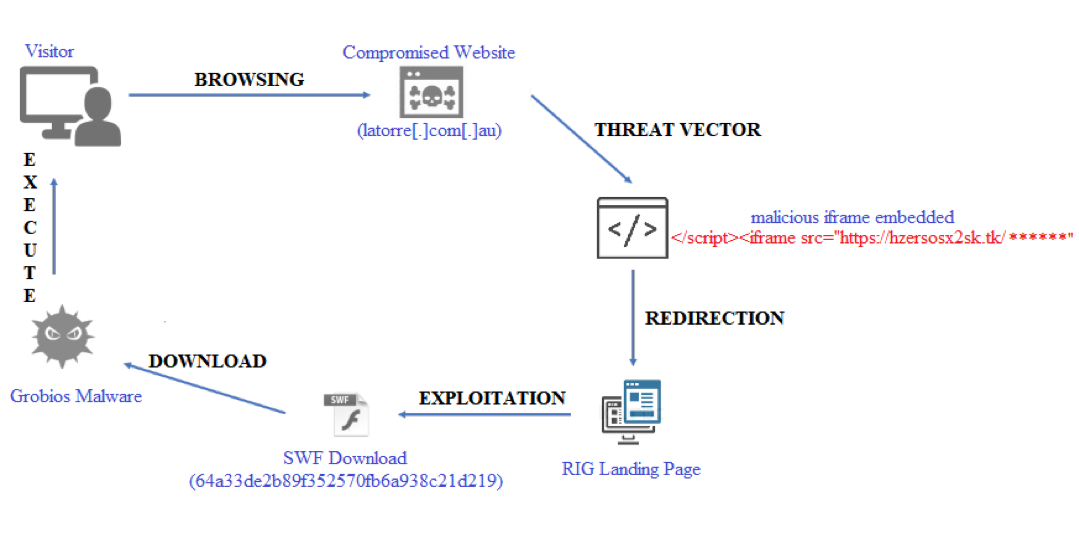
A Deep Dive Into RIG Exploit Kit Delivering Grobios Trojan
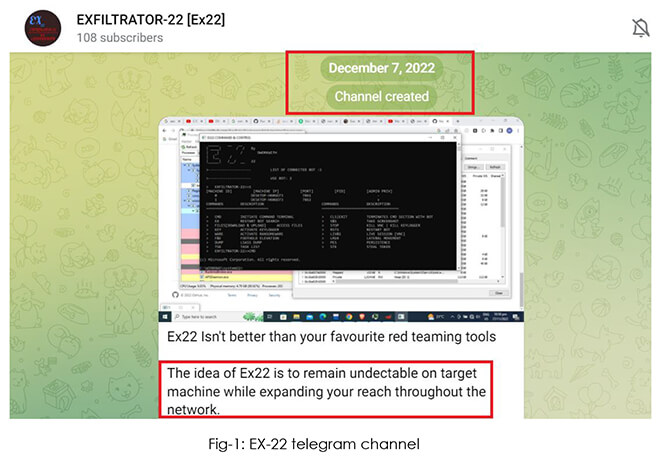
EXFILTRATOR-22 - An Emerging Post-Exploitation Framework - CYFIRMA
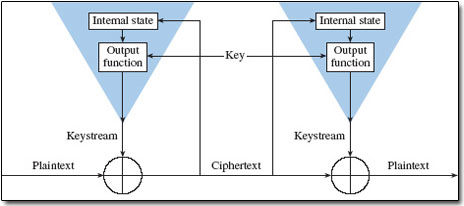
An Overview of Cryptography
de
por adulto (o preço varia de acordo com o tamanho do grupo)