Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
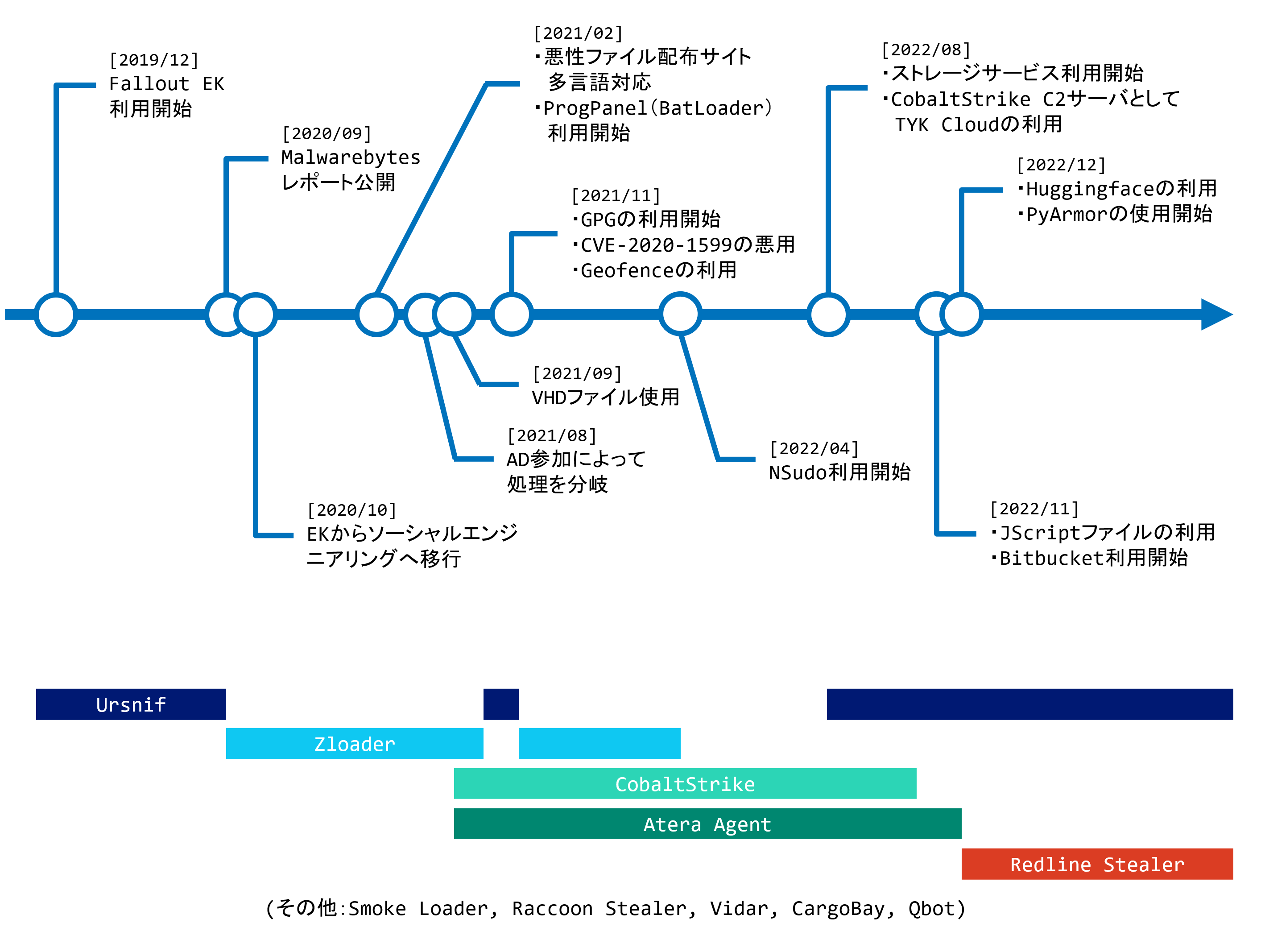
Descrição
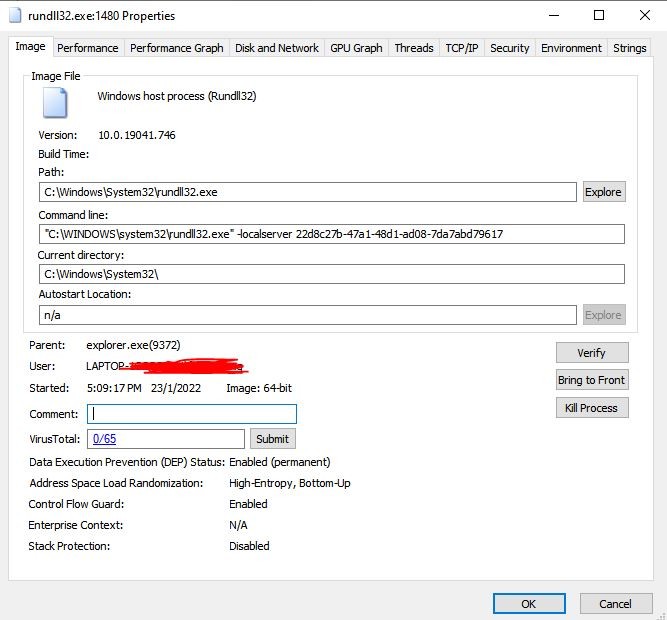
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

Microsoft experts linked Raspberry Robin malware to Evil Corp
Rundll32 Injected with mining malware - Microsoft Community
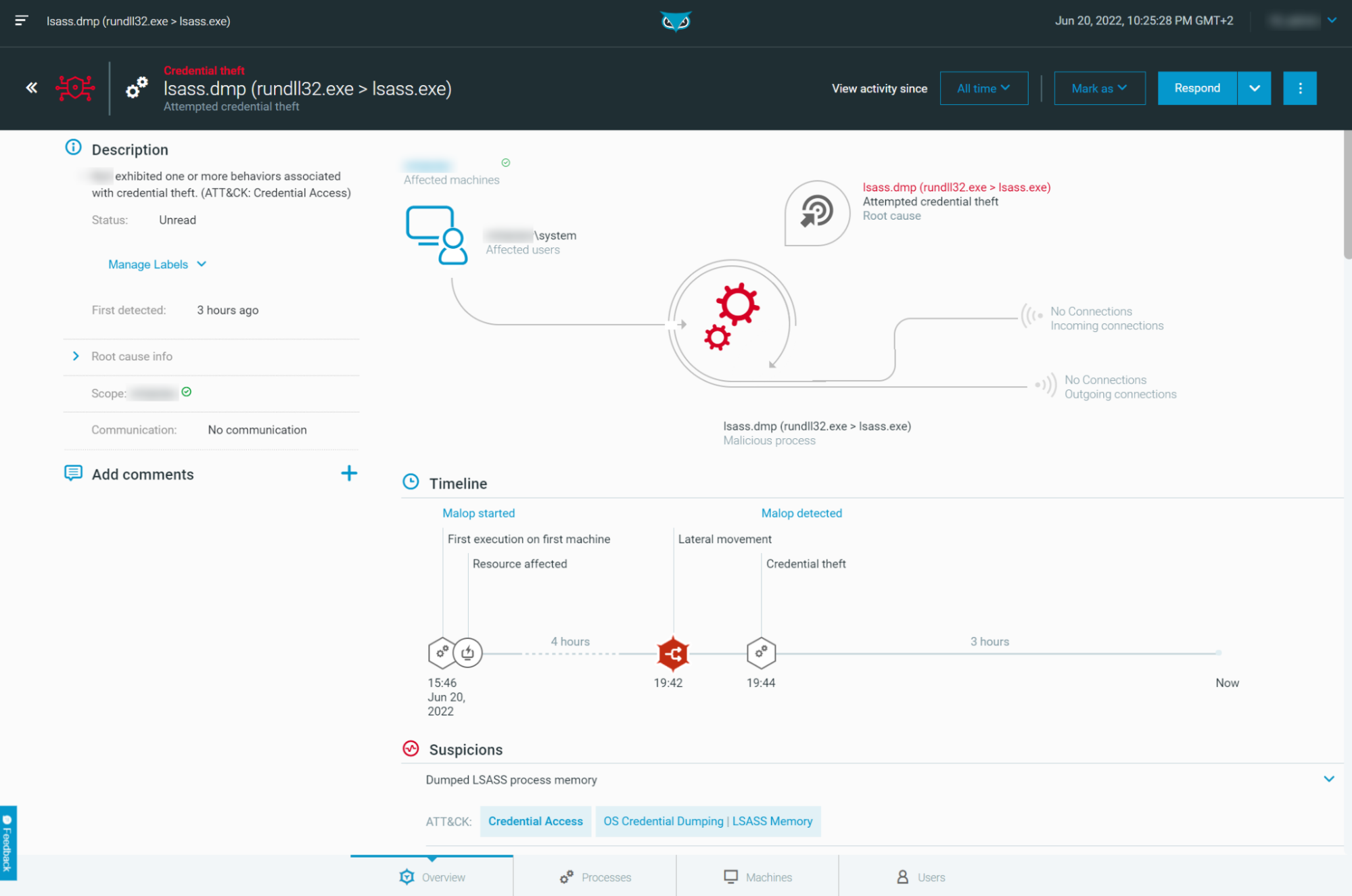
Rundll32: The Infamous Proxy for Executing Malicious Code

Windows Exploitation: rundll32.exe - Hacking Articles
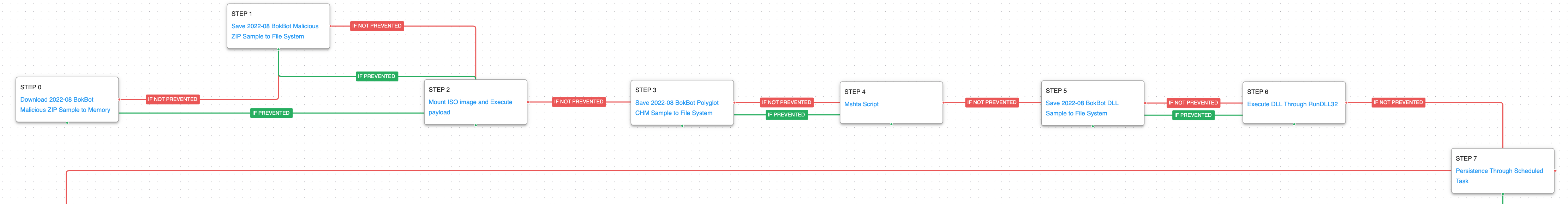
Emulating the Infamous Modular Banking Trojan BokBot - AttackIQ

Detecting IcedID: The Latest Campaign Against Ukrainian Government Bodies - SOC Prime
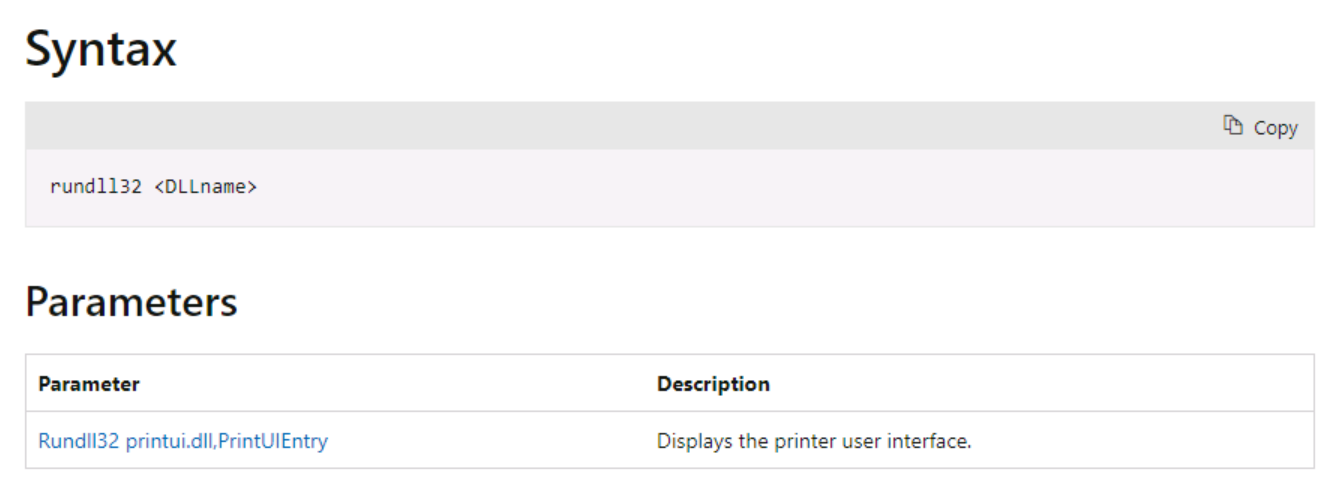
Rundll32: The Infamous Proxy for Executing Malicious Code
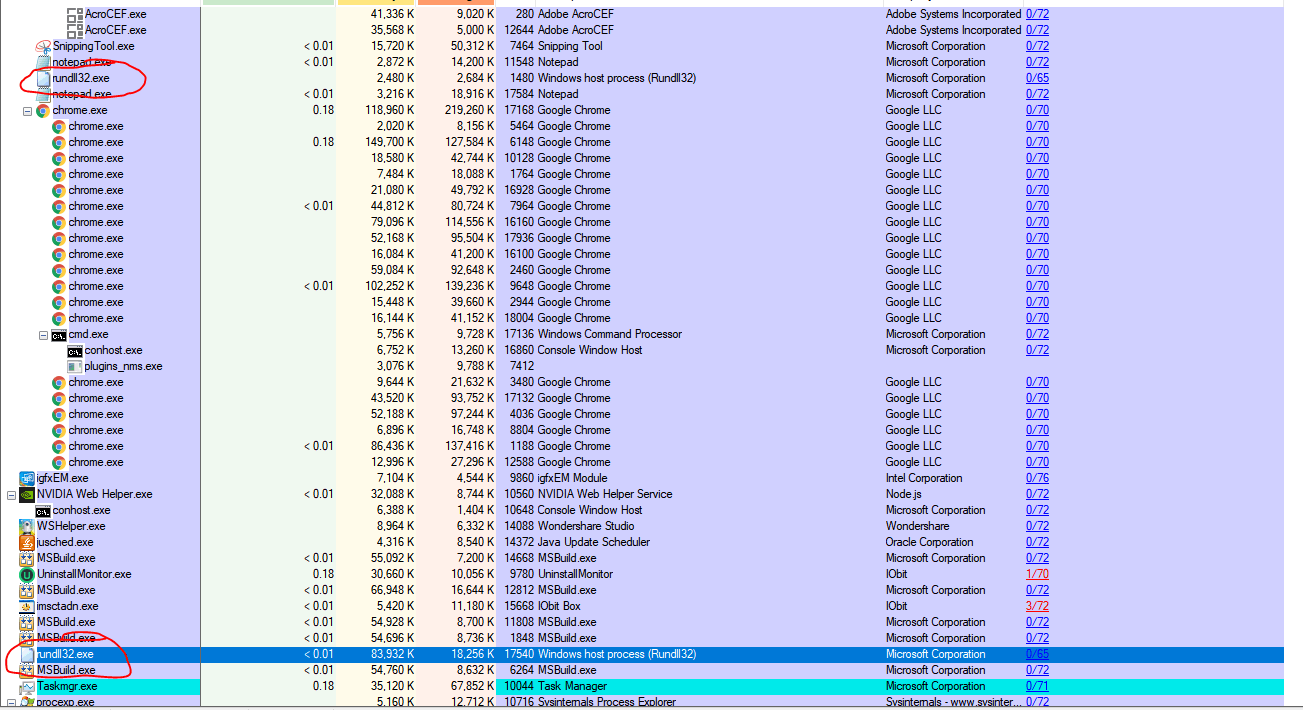
Rundll32 Injected with mining malware - Microsoft Community
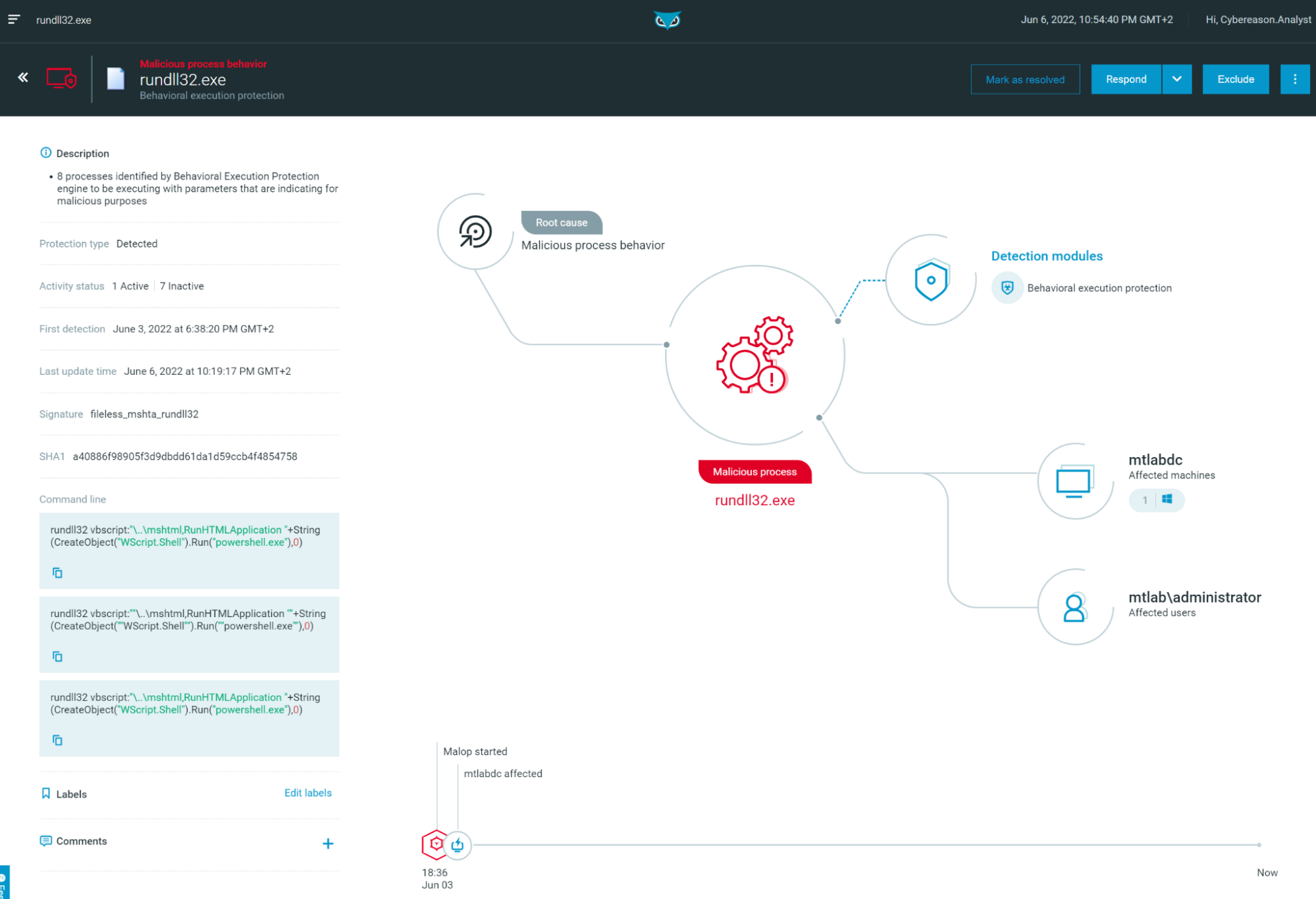
Rundll32: The Infamous Proxy for Executing Malicious Code
Bluepurple Pulse: week ending February 12th - by Ollie
de
por adulto (o preço varia de acordo com o tamanho do grupo)