XSS Filters: Beating Length Limits Using Shortened Payloads
Por um escritor misterioso
Descrição
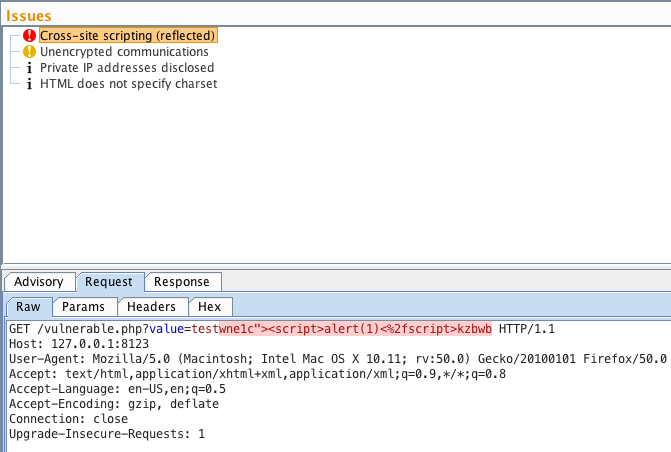
XSS Filters: Beating Length Limits Using Shortened Payloads The most obvious method when attempting to beat a filter that truncates your input to a fixed

PDF) Twenty-two years since revealing cross-site scripting attacks: a systematic mapping and a comprehensive survey

How to Bypass XSS Filters CyberSecurityTV
What are some ways of protecting against cross-site scripting (XSS) injection through cookies? - Quora

reflected xss - How to bypass server side XSS filter for characters like < > / * - Information Security Stack Exchange
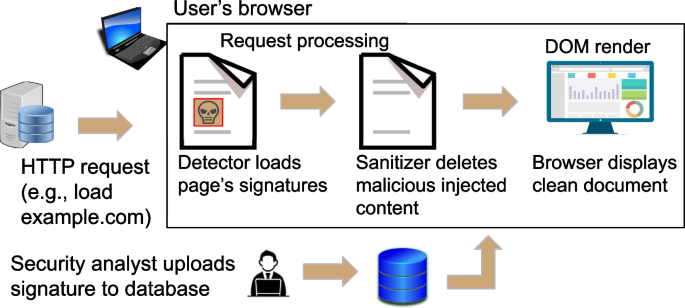
XSnare: application-specific client-side cross-site scripting protection
XSS Filters: Beating Length Limits Using Spanned Payloads - PortSwigger

Security – simpleisbest.co.uk

Minifying XSS. How I bypassed Cross-Site Scripting…, by Jakob Pennington, Taptu

How I tested for CRLF Injection with Akto, by Rohitpatil
XSS Filter Bypass, Escape Parentheses
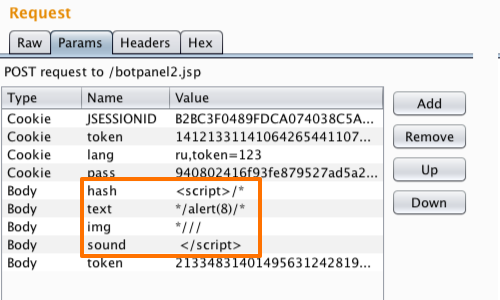
XSS Filters: Beating Length Limits Using Spanned Payloads - PortSwigger

Obfuscated/Polyglot XSS Payloads Simplified with references., by Shaurya Sharma, Cyber Verse

XSS Filter Evasion
GreyNoise Intelligence
Short XSS - Pwning your Browser in 30 Characters or Less
de
por adulto (o preço varia de acordo com o tamanho do grupo)


/cdn.vox-cdn.com/uploads/chorus_asset/file/24062776/STK138_Stream_Kradtke_01.jpg)

