Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights
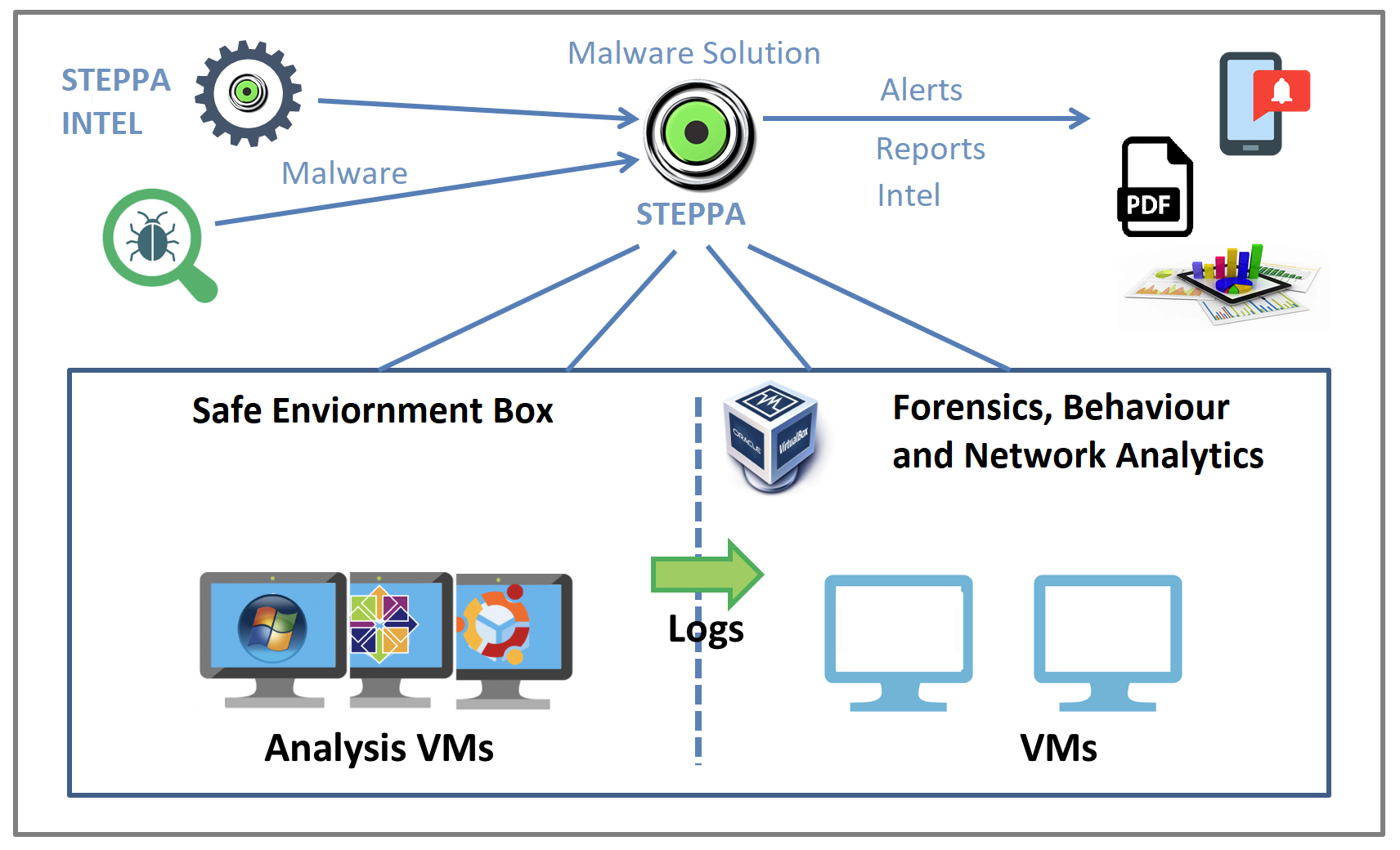
Malware Analysis Solution: Analyze, Detect, and Protect

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
Lab 6-1 Solutions - Practical Malware Analysis [Book]
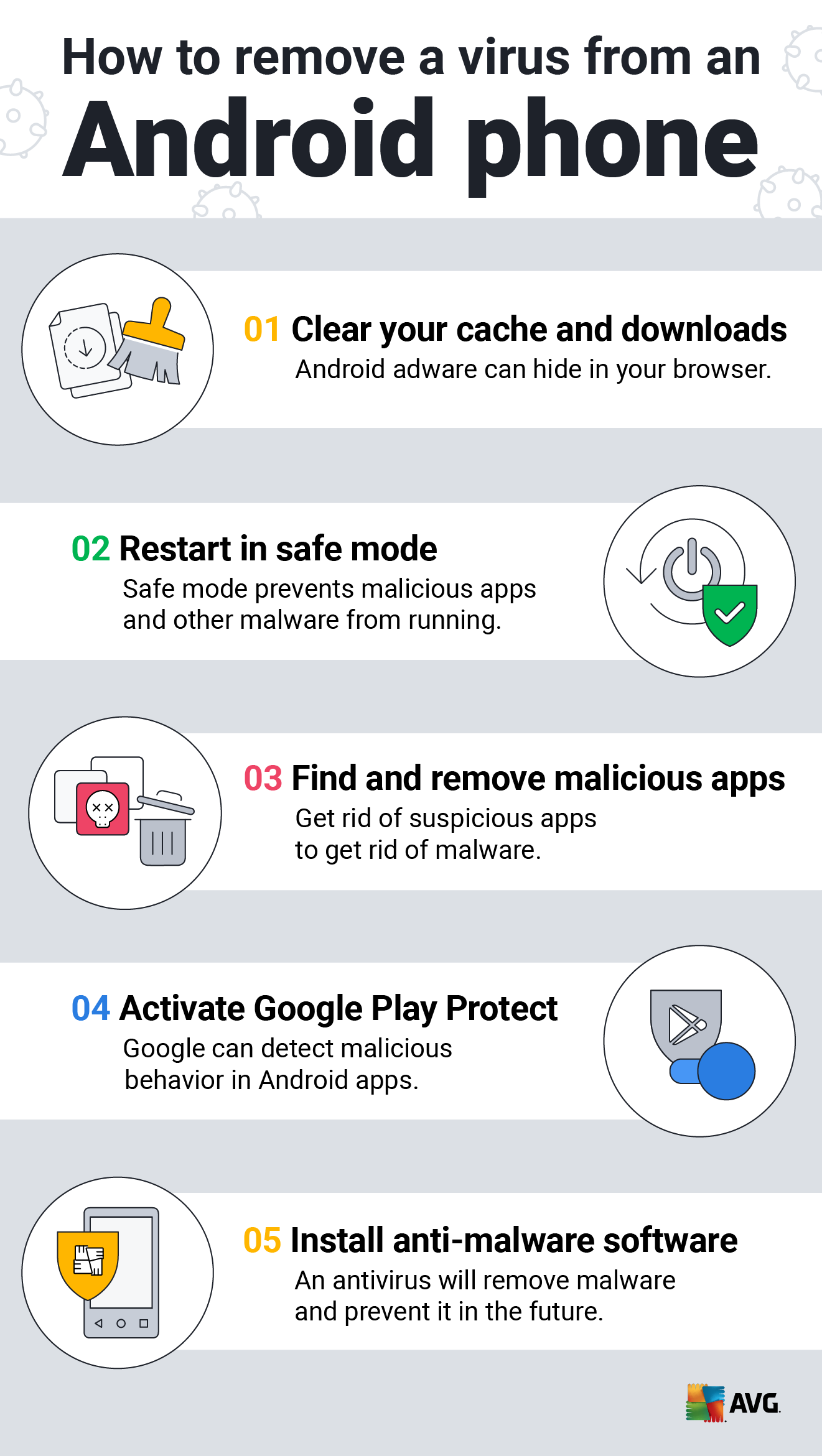
How to Clean an Android or iPhone from Viruses for Free

How to Analyze Malware's Network Traffic in A Sandbox

AlienVault - Open Threat Exchange

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Interactive Online Malware Sandbox

Malware analysis index.html Malicious activity
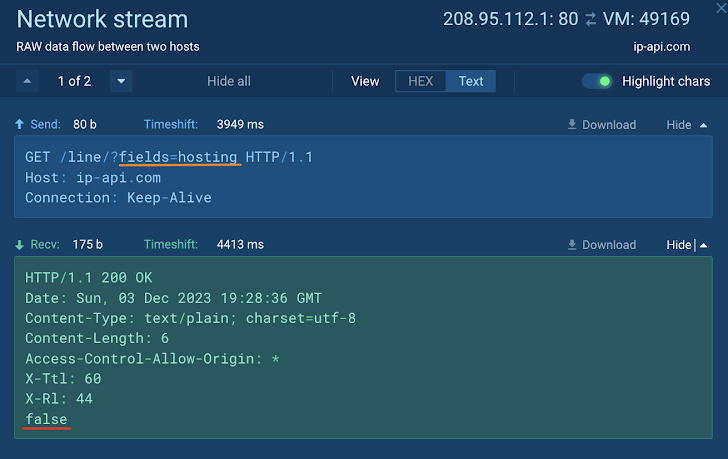
How to Analyze Malware's Network Traffic in A Sandbox
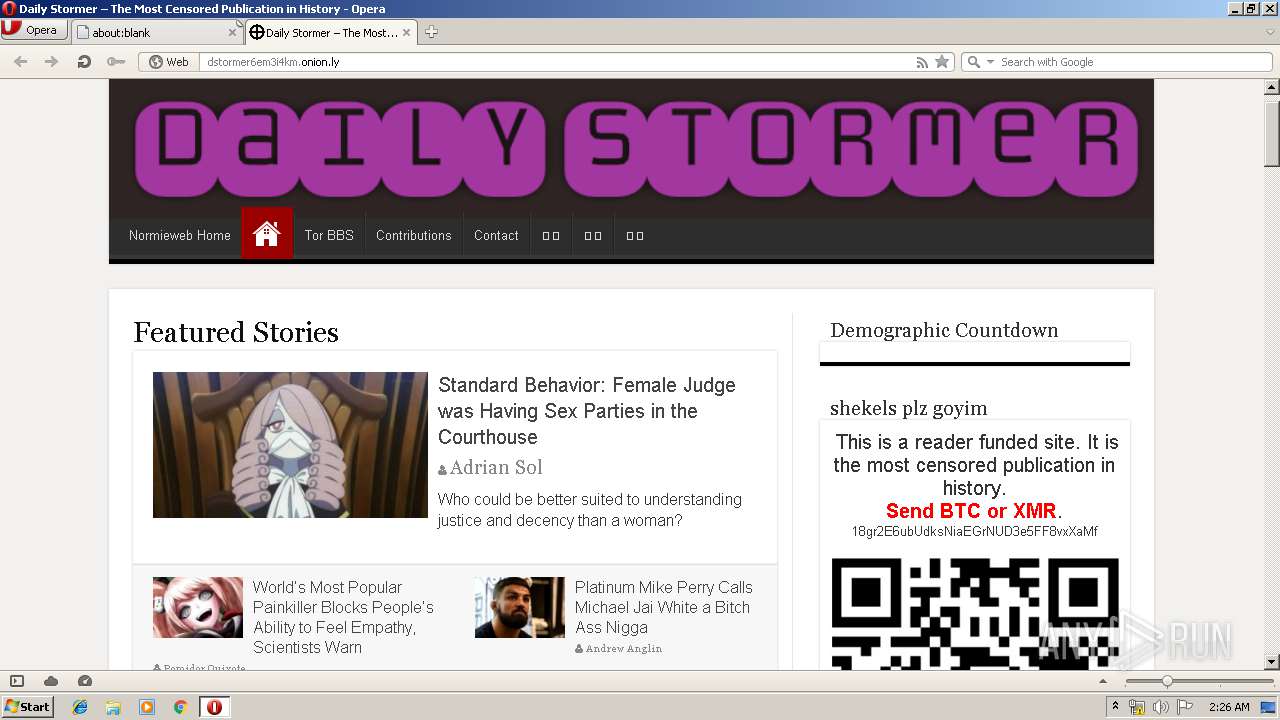
Malware analysis Malicious activity

How to build a malware analysis sandbox with Elastic Security

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
de
por adulto (o preço varia de acordo com o tamanho do grupo)






