Malware analysis Malicious activity
Por um escritor misterioso
Descrição
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware
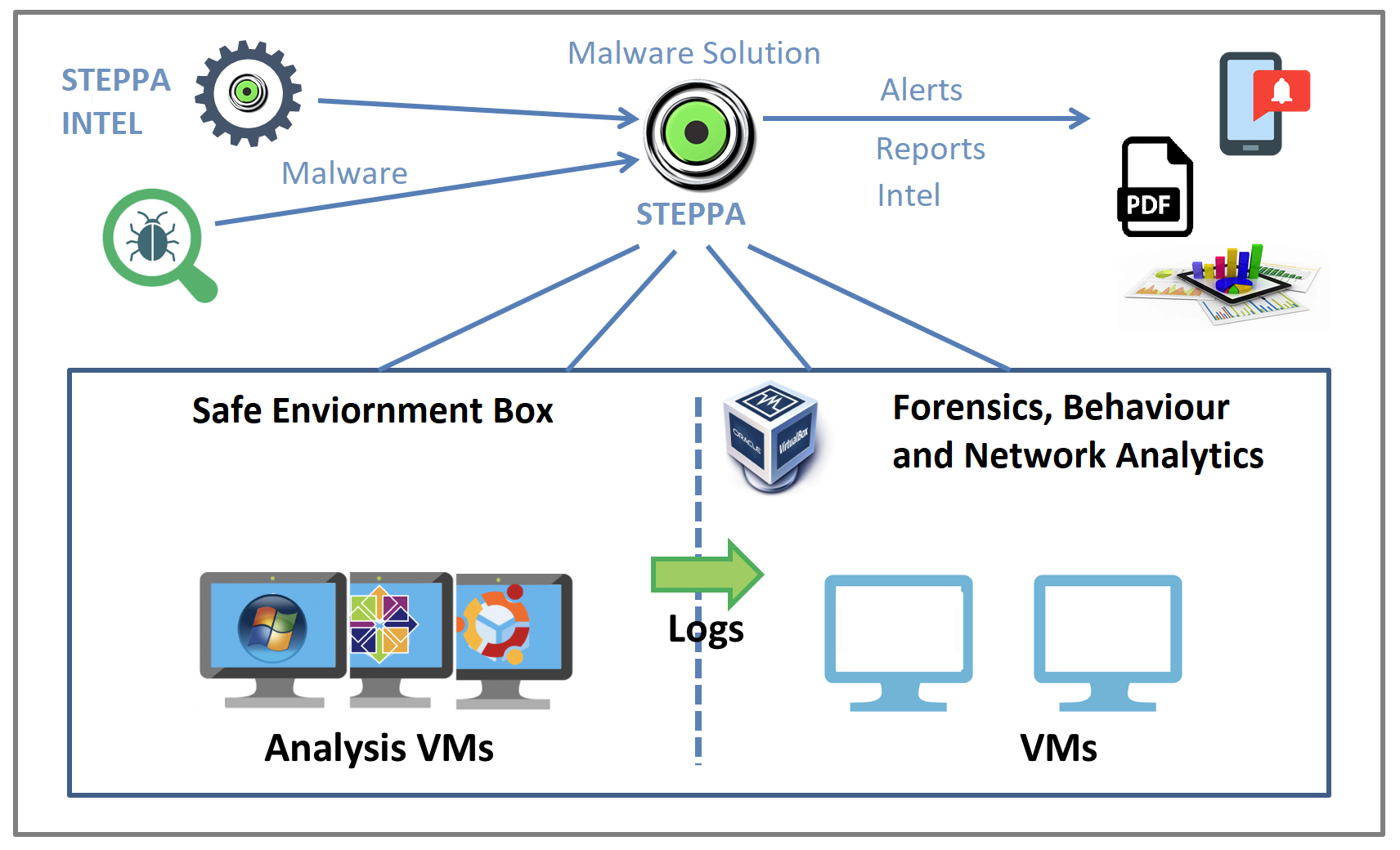
Malware Analysis Solution: Analyze, Detect, and Protect
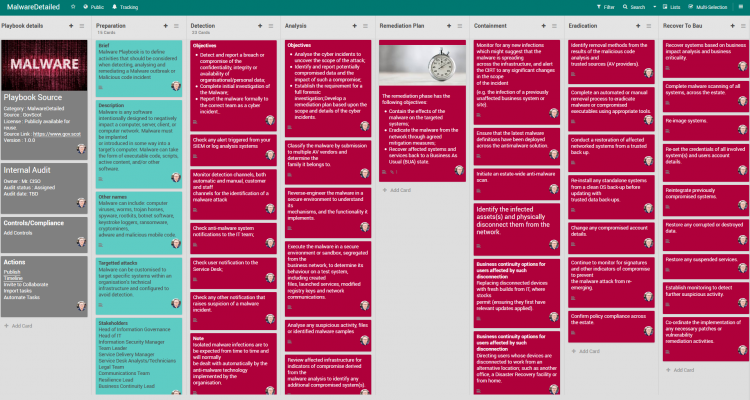
Playbook for Malware outbreak

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Cybersecurity Search Engine
Interactive Online Malware Sandbox

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Rising threats: Cybercriminals unleash 411,000 malicious files daily in 2023
de
por adulto (o preço varia de acordo com o tamanho do grupo)