Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
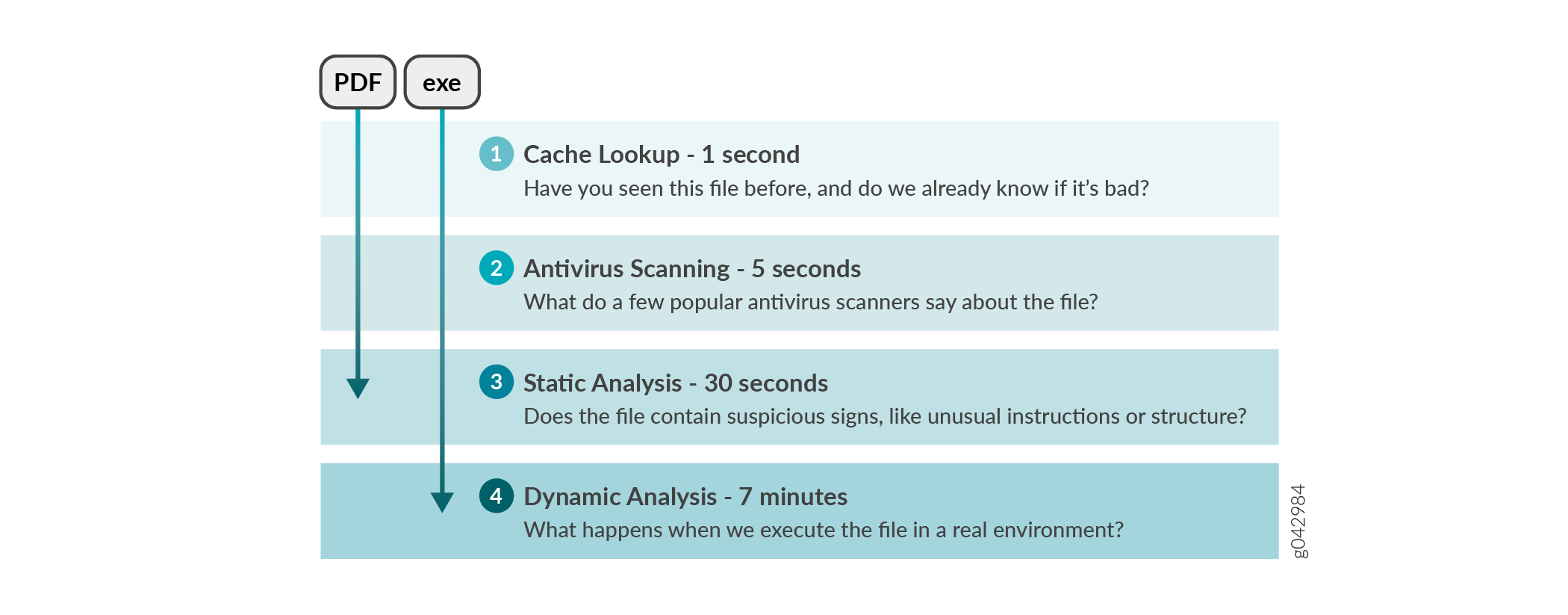
How is Malware Analyzed and Detected?, ATP Cloud

Malware Analysis: Steps & Examples - CrowdStrike

Windows Servers Security: How to Look for Suspicious Activities
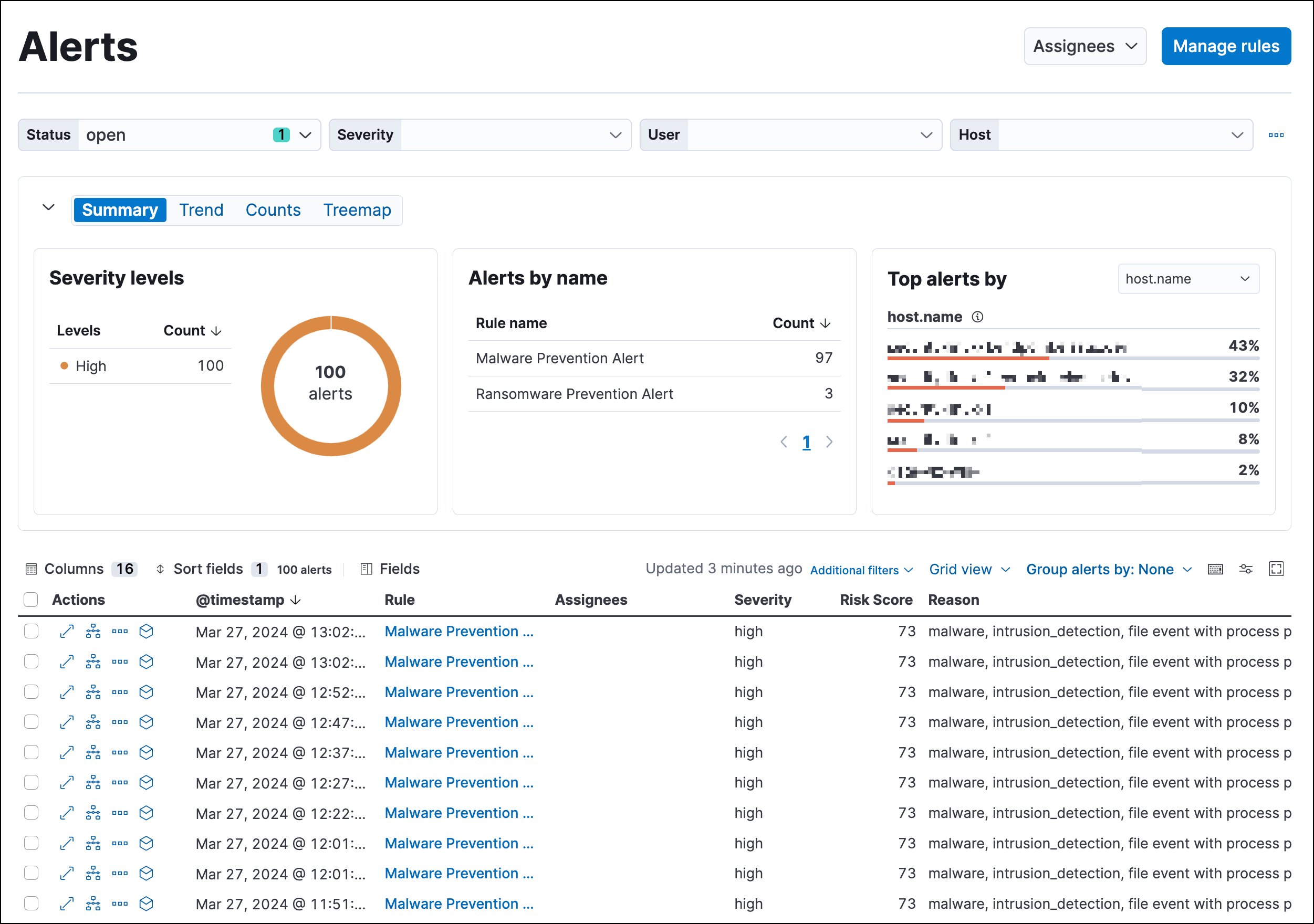
Detections and alerts, Elastic Security Solution [8.11]

Malware Detection & Top Techniques Today

US Cyber Command, DHS-CISA release Russian malware samples tied to
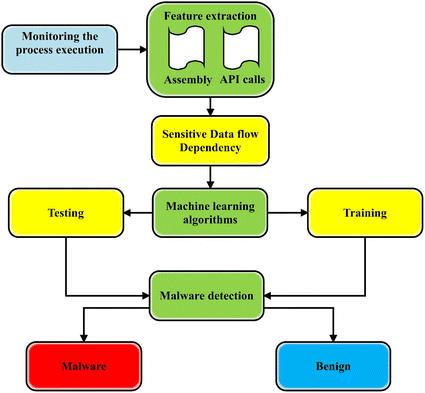
A state-of-the-art survey of malware detection approaches using
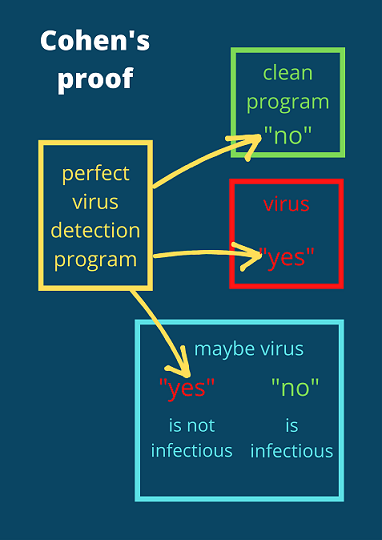
The real reason why malware detection is hard

How to Analyze Malware Infections?
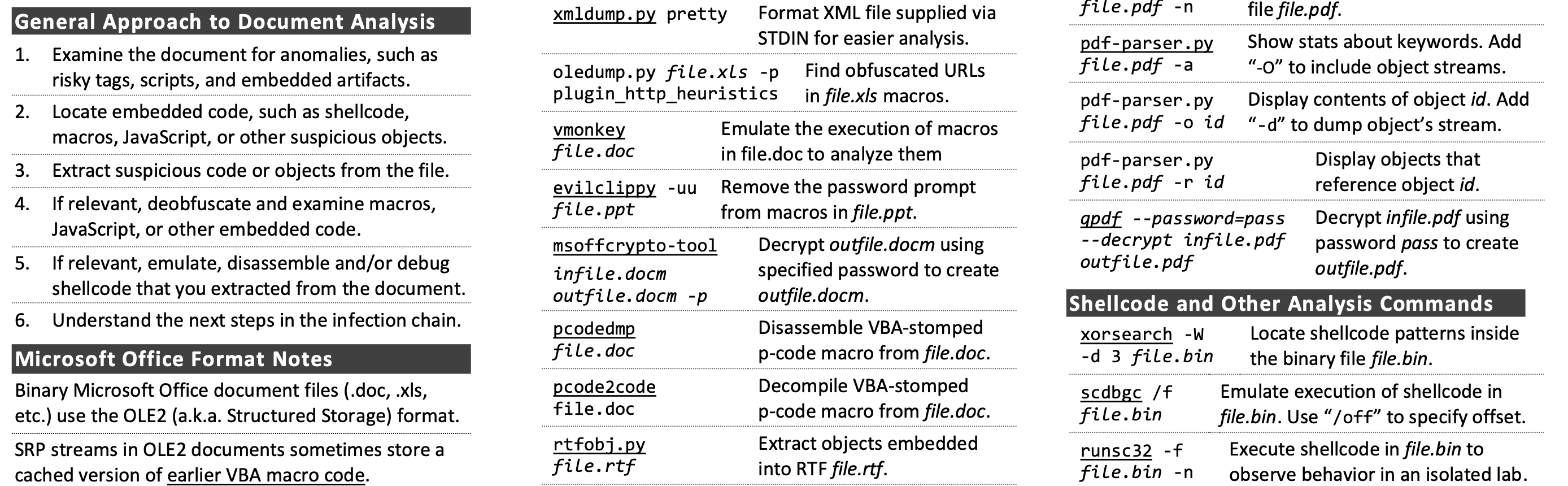
Analyzing Malicious Documents Cheat Sheet
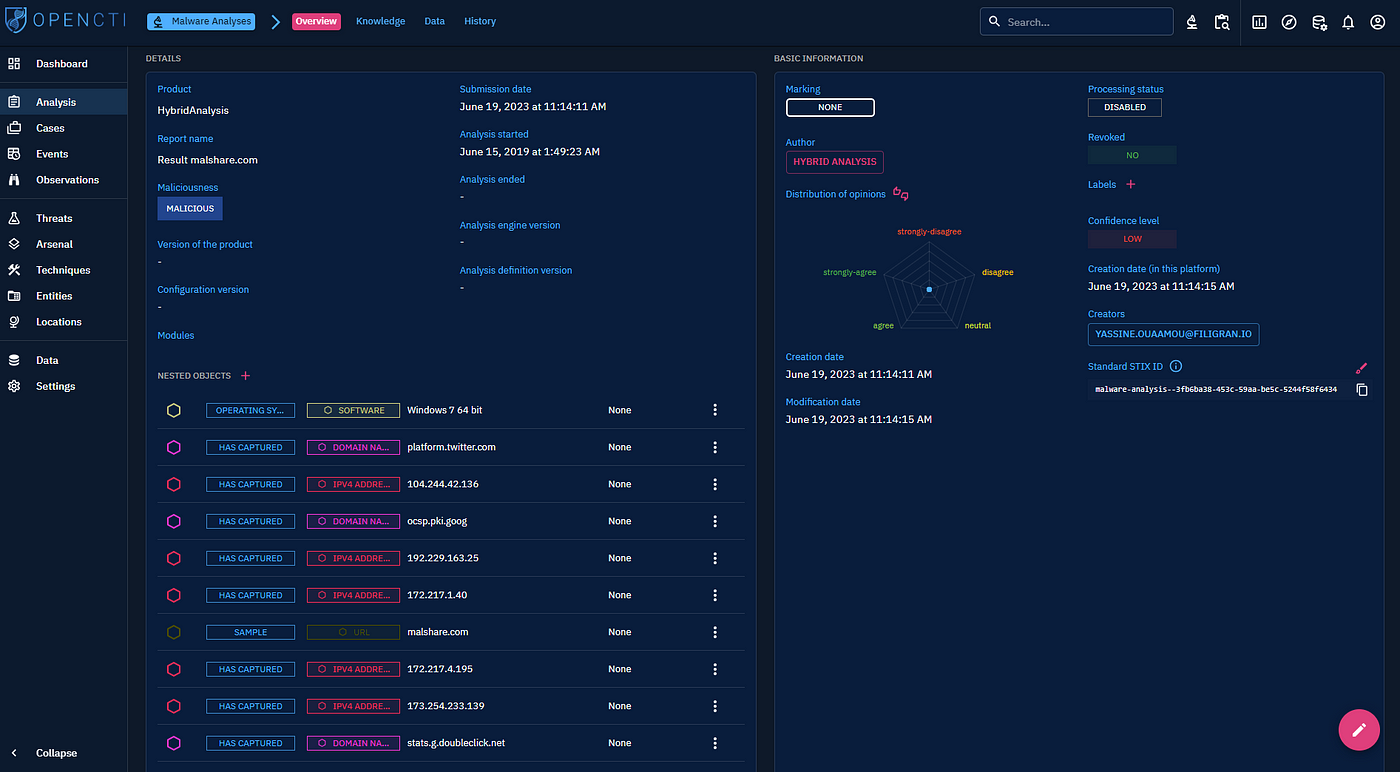
Introducing malware analysis: enhance your cybersecurity triage
de
por adulto (o preço varia de acordo com o tamanho do grupo)







