PDF] Implications of Malicious 3 D Printer Firmware
Por um escritor misterioso
Descrição
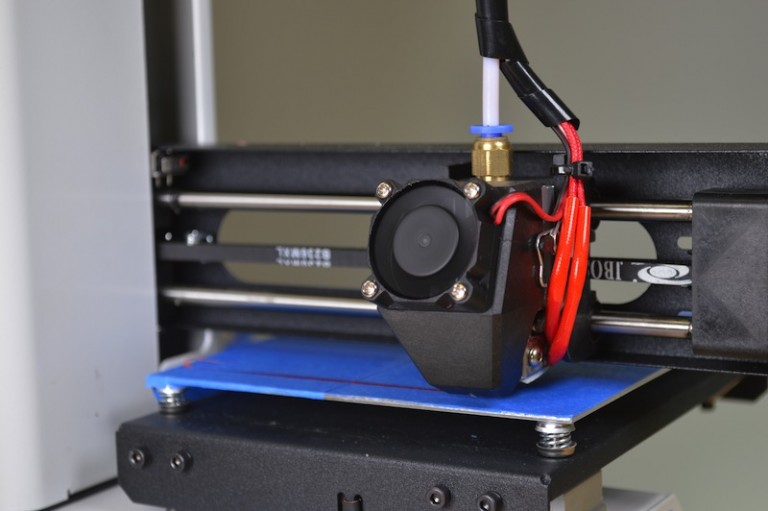
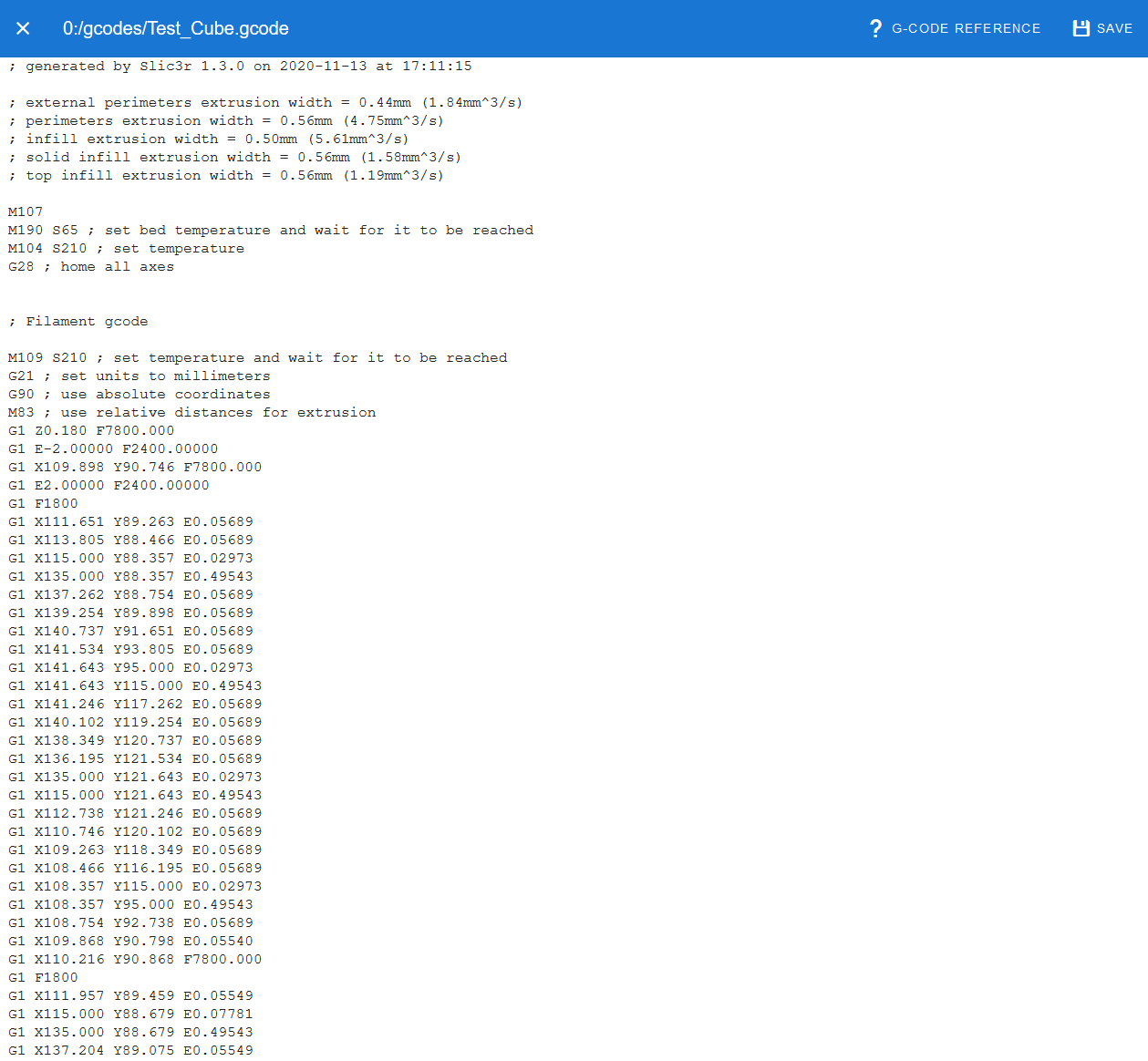
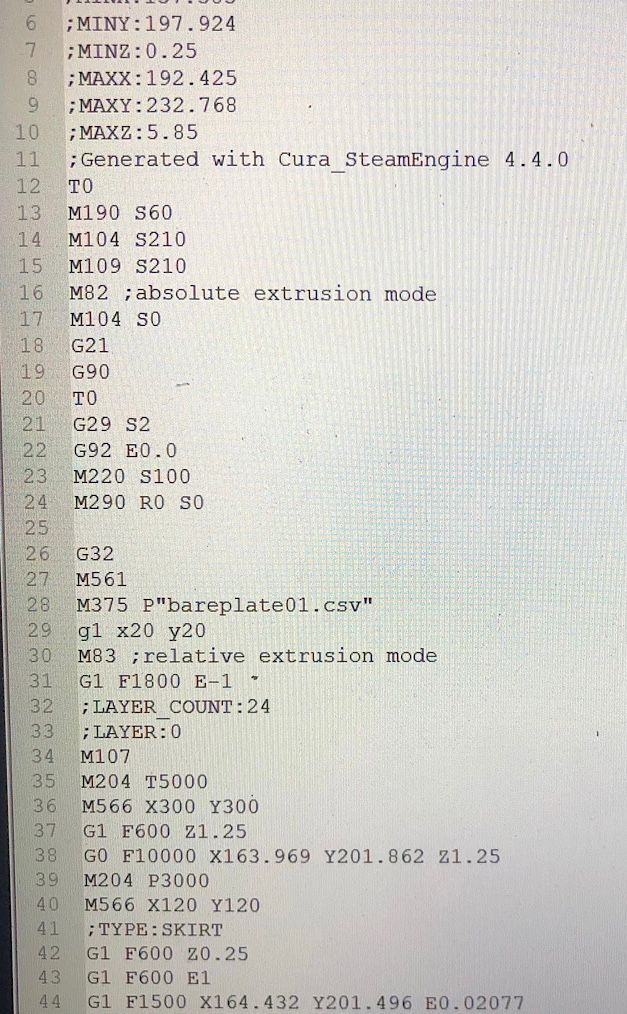
This research develops and implements malicious code using Printrbot’s branch of the open source Marlin 3D printer firmware to provide an initial assessment of potential effects malicious firmware can have on a 3D printed object and documents a potential vulnerability that impacts 3D product output using 3D printers firmware. The utilization of 3D printing technology within the manufacturing process creates an environment that is potentially conducive to malicious activity. Previous research in 3D printing focused on attack vector identification and intellectual property protection. This research develops and implements malicious code using Printrbot’s branch of the open source Marlin 3D printer firmware. Implementations of the malicious code were activated based on a specified printer command sent from a desktop application. The malicious firmware successfully ignored incoming print commands for a printed 3D model, substituted malicious print commands for an alternate 3D model, and manipulated extruder feed rates. The research contribution is three-fold. First, this research provides an initial assessment of potential effects malicious firmware can have on a 3D printed object. Second, it documents a potential vulnerability that impacts 3D product output using 3D printer firmware. Third, it provides foundational grounding for future research in malicious 3D printing process activities.
![PDF] Implications of Malicious 3 D Printer Firmware](https://i.pcmag.com/imagery/articles/04gbkycwMLsiwVhPxh71mEZ-1.fit_lim.size_308x350.v_1569470611.jpg)
Read PDF Files Safely: Here is How
![PDF] Implications of Malicious 3 D Printer Firmware](https://d3i71xaburhd42.cloudfront.net/c7bdbb7991db5daef129db2de616bbc7027a43f3/3-Figure1-1.png)
PDF] Implications of Malicious 3 D Printer Firmware
![PDF] Implications of Malicious 3 D Printer Firmware](https://www.researchgate.net/profile/William-Glisson/publication/317418390/figure/fig1/AS:614253786562560@1523460923205/Rate-Value-The-malicious-rate-variable-is-then-programmed-into-the-plan-buffer-line_Q320.jpg)
PDF) Implications of Malicious 3D Printer Firmware
![PDF] Implications of Malicious 3 D Printer Firmware](https://ee.cdnartwhere.eu/wp-content/uploads/import/default/files/sites/default/files/images/2017-08-16-s20_3d_printing_additive_manufacturing_intrusion_security_verification-600x400-c-default.jpg)
Defeating cyberattacks on 3D printers
How To Successfully Flash Your 3D Printer's Firmware
![PDF] Implications of Malicious 3 D Printer Firmware](https://hackaday.com/wp-content/uploads/2019/02/3d-printer-id.jpg?w=640)
Identifying A 3D Printer From A 3D Print
![PDF] Implications of Malicious 3 D Printer Firmware](https://www.mdpi.com/sensors/sensors-23-09886/article_deploy/html/images/sensors-23-09886-g001.png)
Sensors, Free Full-Text
![PDF] Implications of Malicious 3 D Printer Firmware](https://eclypsium.com/wp-content/uploads/feature_image_top5fw.jpg)
As firmware-level threats continue to gain popularity in the wild, security teams need to understand how these threats work and the real-world risks they pose to an organization's security. Updated for 2021
![PDF] Implications of Malicious 3 D Printer Firmware](https://image.slidesharecdn.com/implementationandimplicationsofastealthhard-drivebackdoor-131002080619-phpapp01/85/implementation-and-implications-of-a-stealth-hard-drive-backdoor-1-320.jpg?cb=1668315332)
Implementation and implications of a stealth hard drive backdoor
de
por adulto (o preço varia de acordo com o tamanho do grupo)