Transfer files (Post explotation) - CheatSheet – ironHackers
Por um escritor misterioso
Descrição
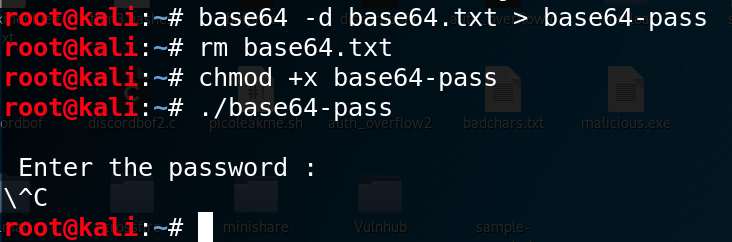
Once shell is achieved in a target it is important the transfer of files between the victim machine and the attacker since many times we will need to upload files as automatic tools or exploits or download victim’s files to analyze them, reversing, etc. In this post we will see a Cheatsheet of some of […]
Almost) All The Ways to File Transfer, by PenTest-duck
Hack the Box: Shocker — Writeup. Shocker is an easy-rated retired

Certified-Ethical-Hacker-(CEH-v11)-Cheat-Sheet - Exam cheat sheet

File Transfer Cheatsheet: Windows and Linux - Hacking Articles

Reddit Hit by Cyberattack that Allowed Hackers to Steal Source Code

File Transfer Cheatsheet: Windows and Linux - Hacking Articles
How to Hack Android Using Kali (Remotely) « Null Byte :: WonderHowTo

CEH Cheat Sheet - Certified Ethical Hacking v10 & v11
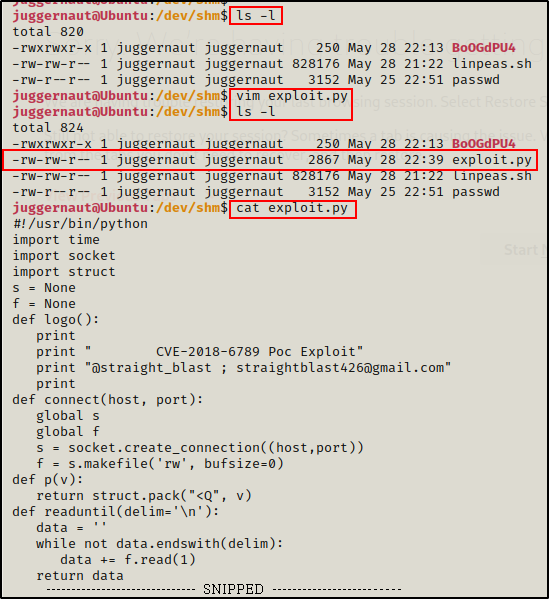
Linux File Transfers for Hackers - Juggernaut-Sec

Hackers Bypass Firewalls Restrictions Using CloudFlare Tunnels

File Transfer Cheatsheet: Windows and Linux - Hacking Articles

Almost) All The Ways to File Transfer, by PenTest-duck
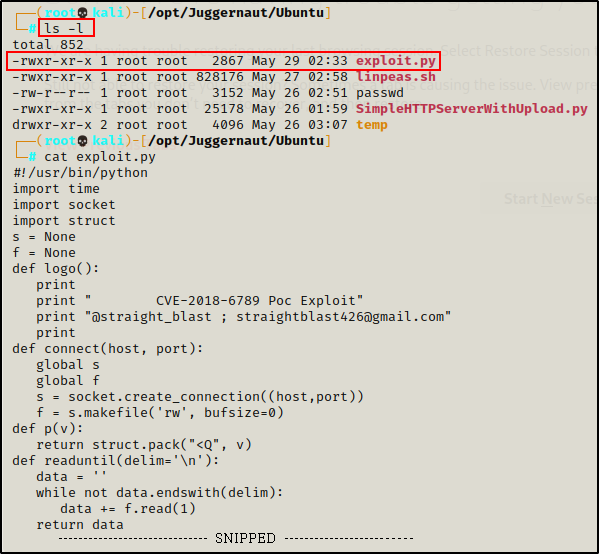
Linux File Transfers for Hackers - Juggernaut-Sec
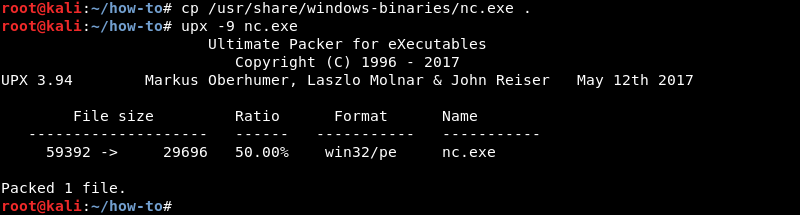
Post Exploitation File Transfers on Windows the Manual Way
de
por adulto (o preço varia de acordo com o tamanho do grupo)