Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Descrição
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

PyCon AU 2012 - Debugging Live Python Web Applications

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend

testar – scriptless testing through graphical user interface - Vos - 2021 - Software Testing, Verification and Reliability - Wiley Online Library

2022-2023 College Catalog by Honolulu Community College - Issuu
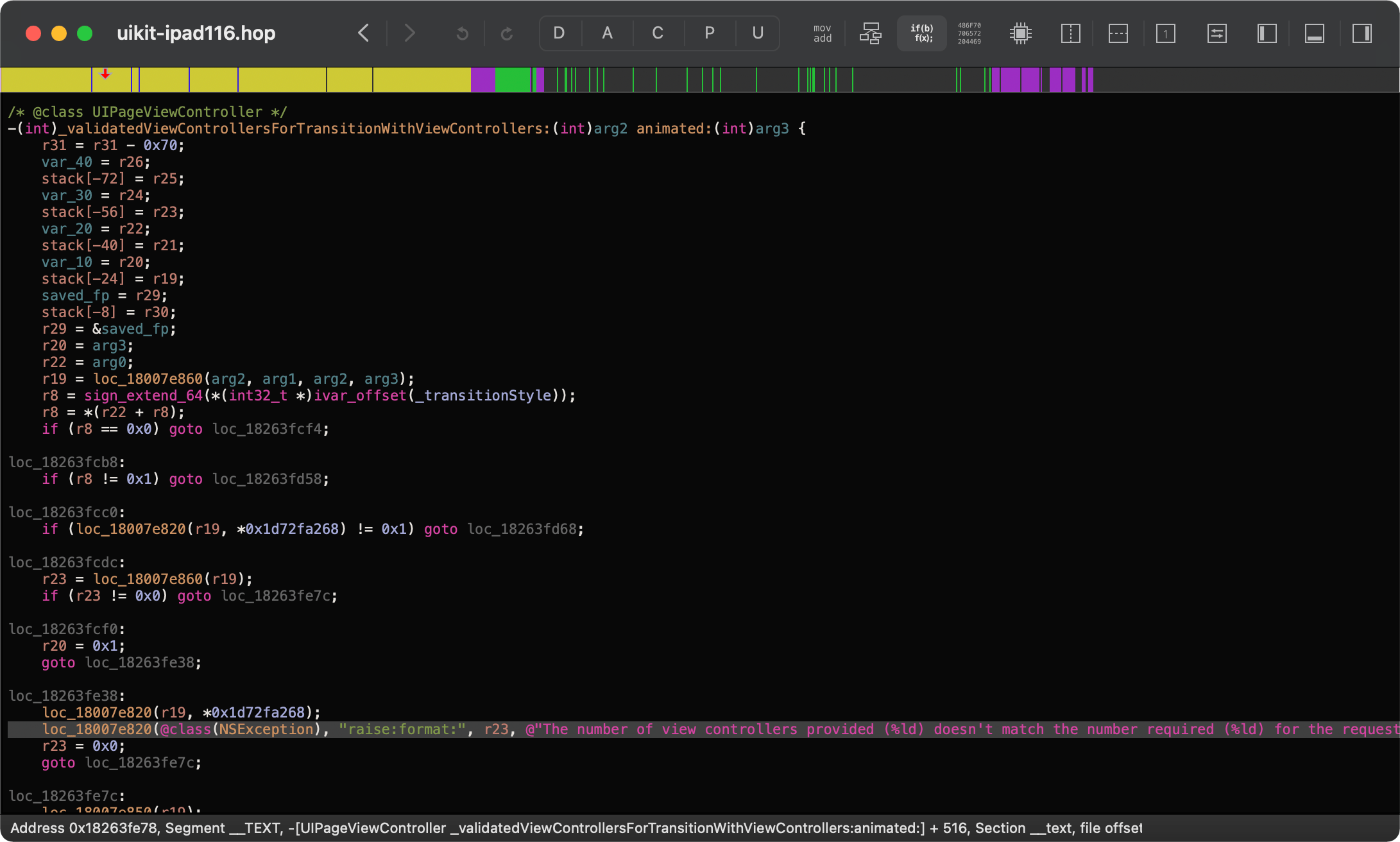
Reverse Engineering UIKit to Fix Our Top Crash

Mastering Malware Analysis
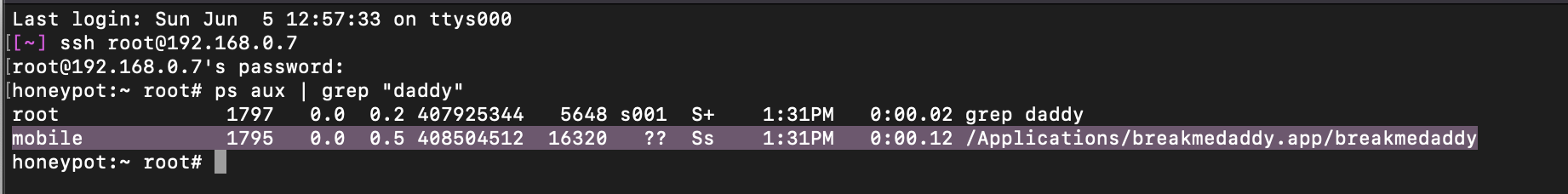
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I

Kodeco Learn iOS, Android & Flutter

TSC Summit #3 - Reverse engineering and anti debugging techniques

Advanced Apple Debugging & Reverse Engineering (3rd Edition) - 2018

GitHub - mikeroyal/Apple-Silicon-Guide: Apple Silicon Guide. Learn all about the A17 Pro, A16 Bionic, R1, M1-series, M2-series, and M3-series chips. Along with all the Devices, Operating Systems, Tools, Gaming, and Software that
Tampering and Reverse Engineering on iOS - OWASP MASTG

Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started
de
por adulto (o preço varia de acordo com o tamanho do grupo)
.jpg)