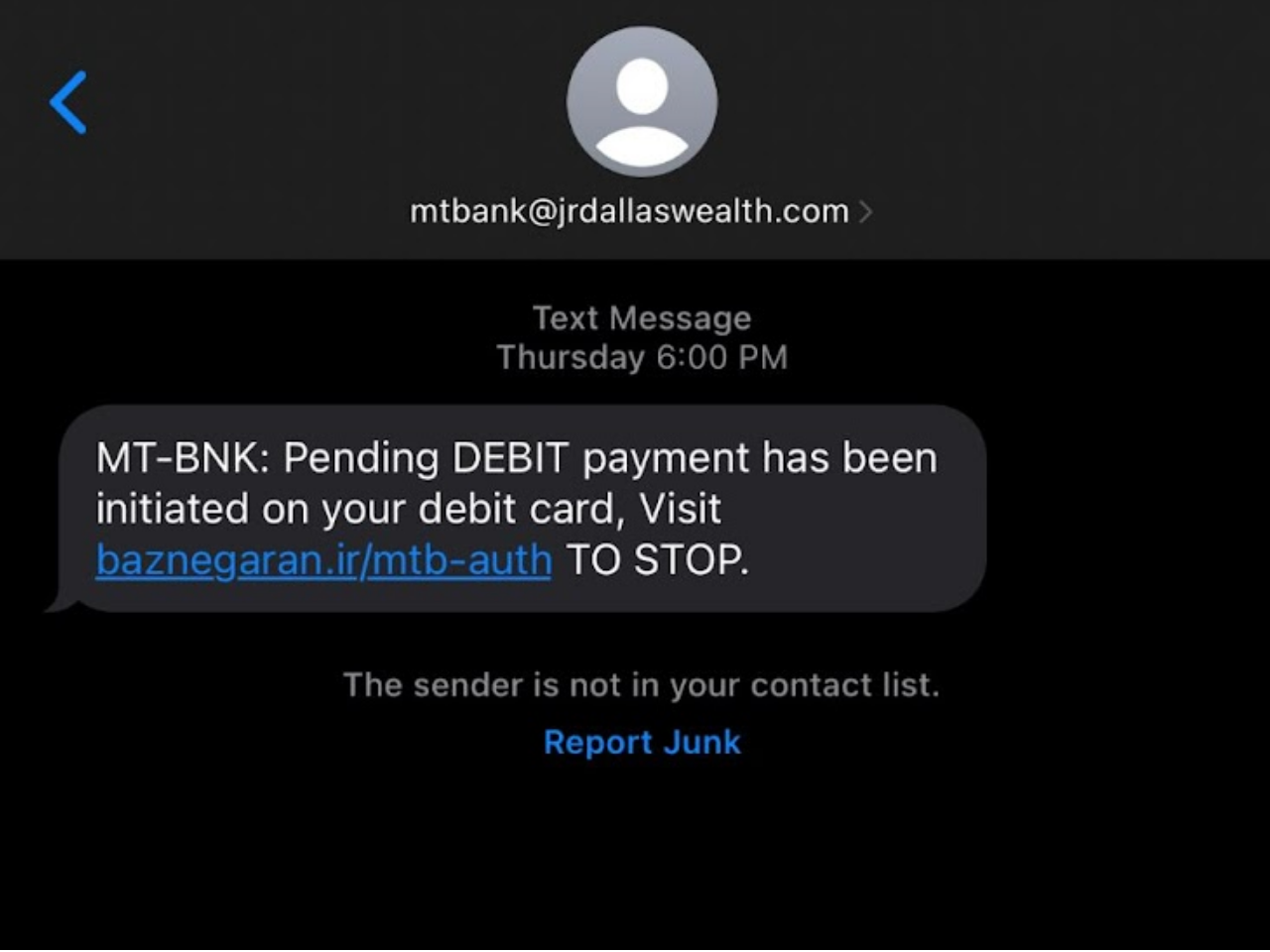
11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Descrição
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.
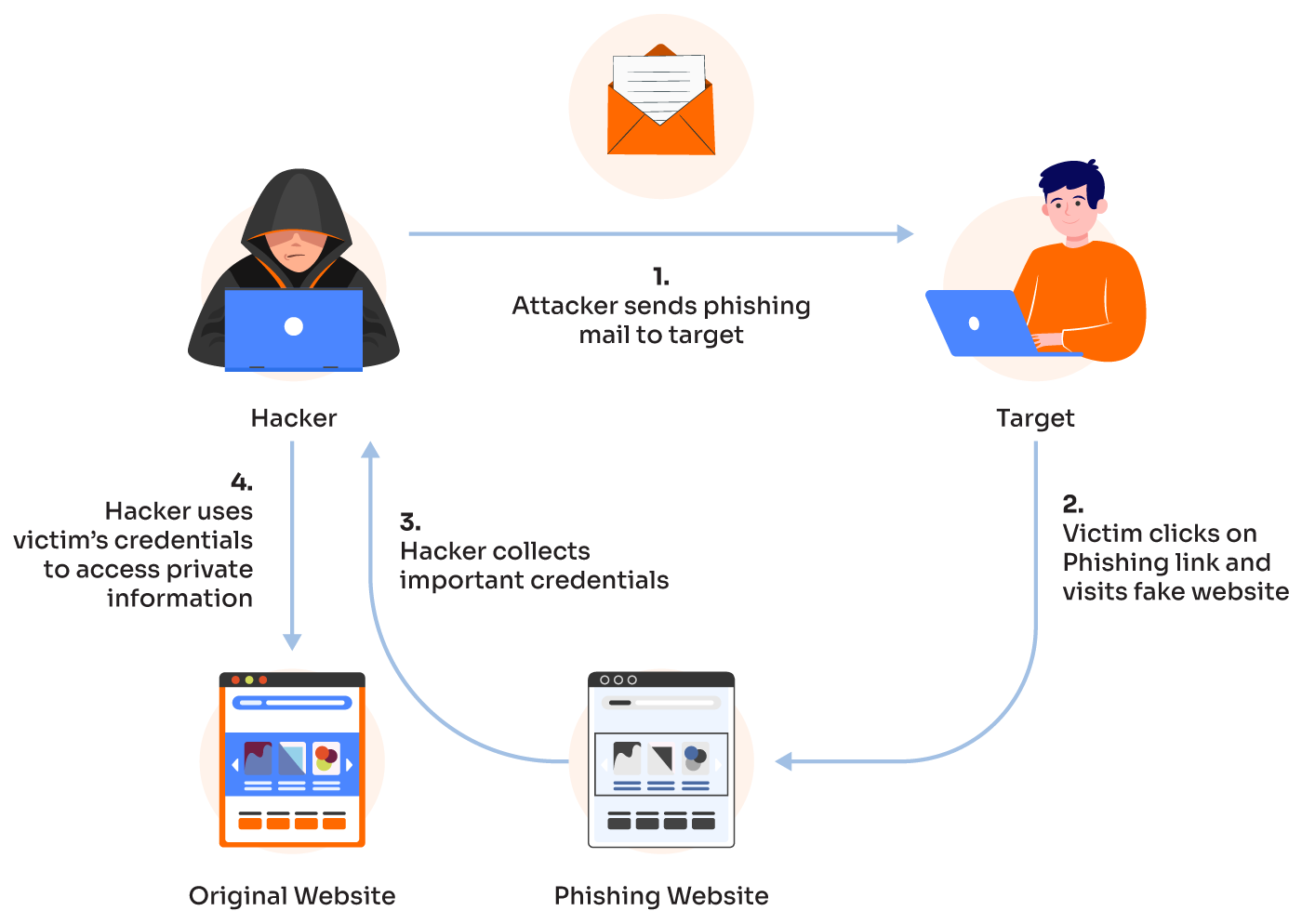
Complete Guide to Phishing: Techniques & Mitigations - Valimail
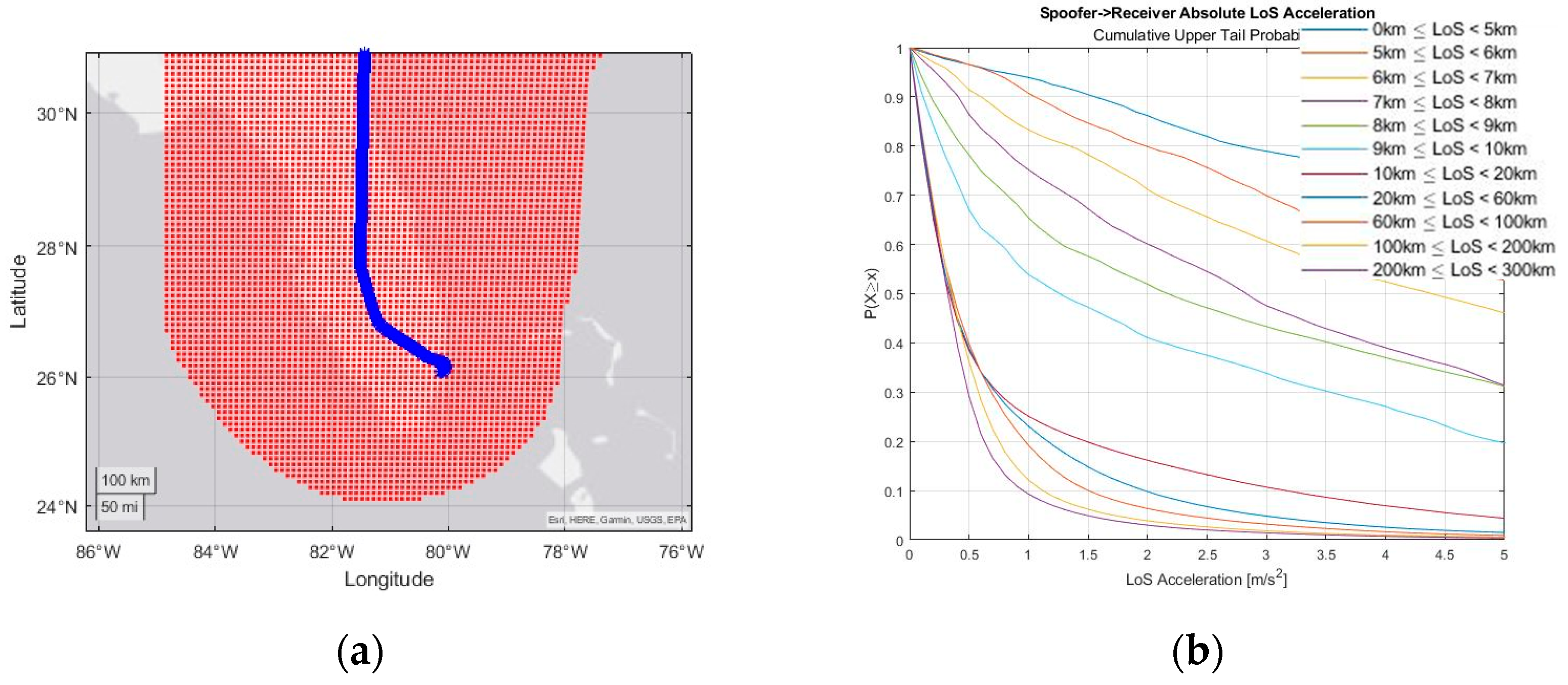
Technologies, Free Full-Text
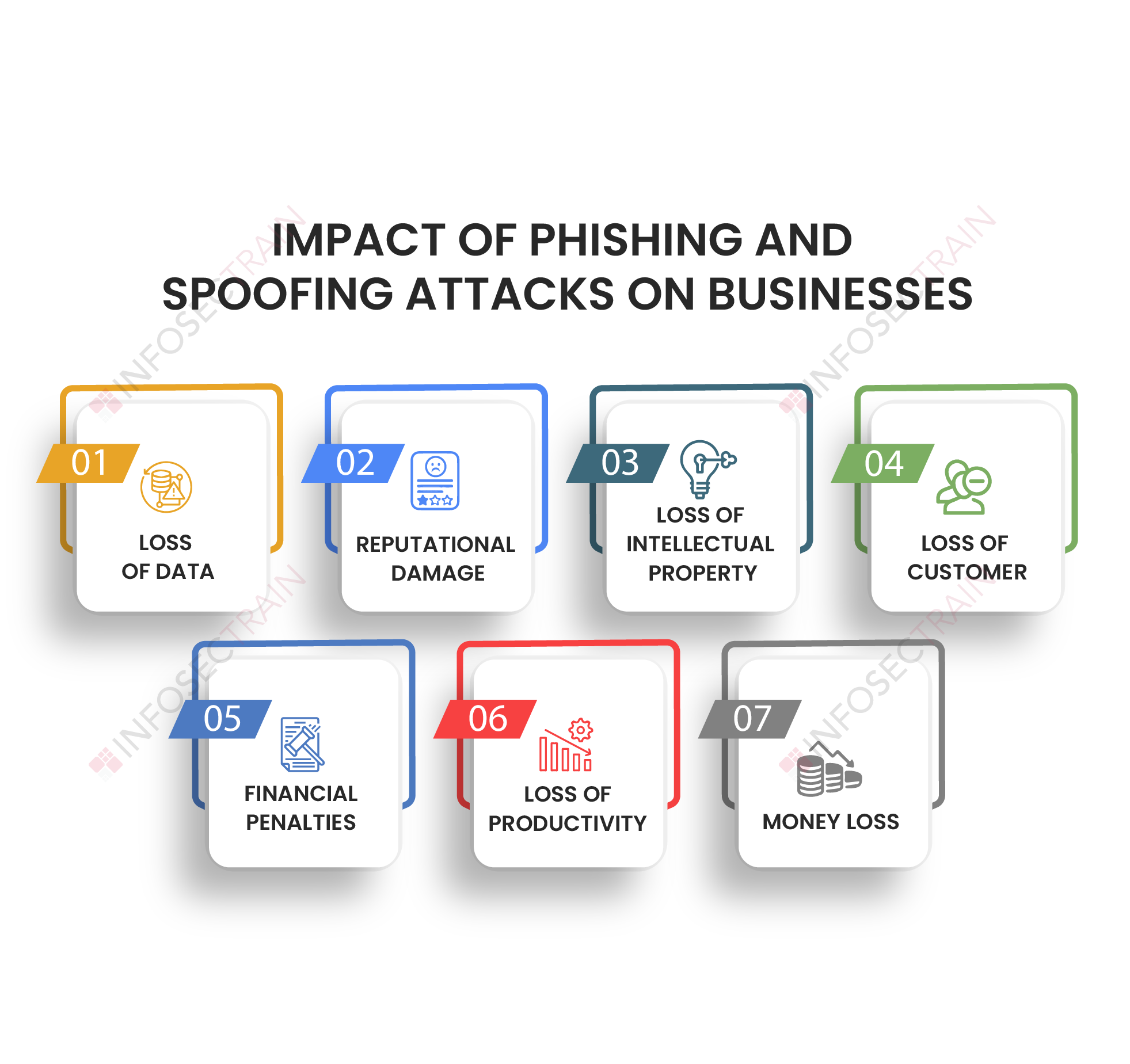
How do Phishing and Spoofing Attacks Impact Businesses?

Types of Cyber Attacks You Should Be Aware of in 2024

What is Spoofing?, Examples & Prevention
Awareness Of Different Types Of Spoofing Attacks Can Keep Your
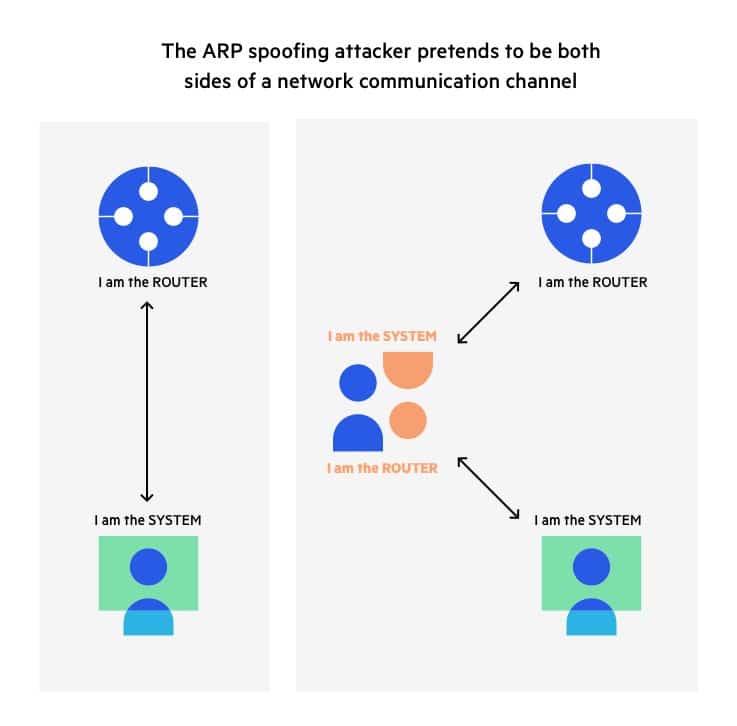
What is ARP Spoofing, ARP Cache Poisoning Attack Explained

What is Spoofing?, Examples & Prevention

20 types of phishing attacks + phishing examples - Norton
de
por adulto (o preço varia de acordo com o tamanho do grupo)