Suspicious User Controls
Por um escritor misterioso
Descrição
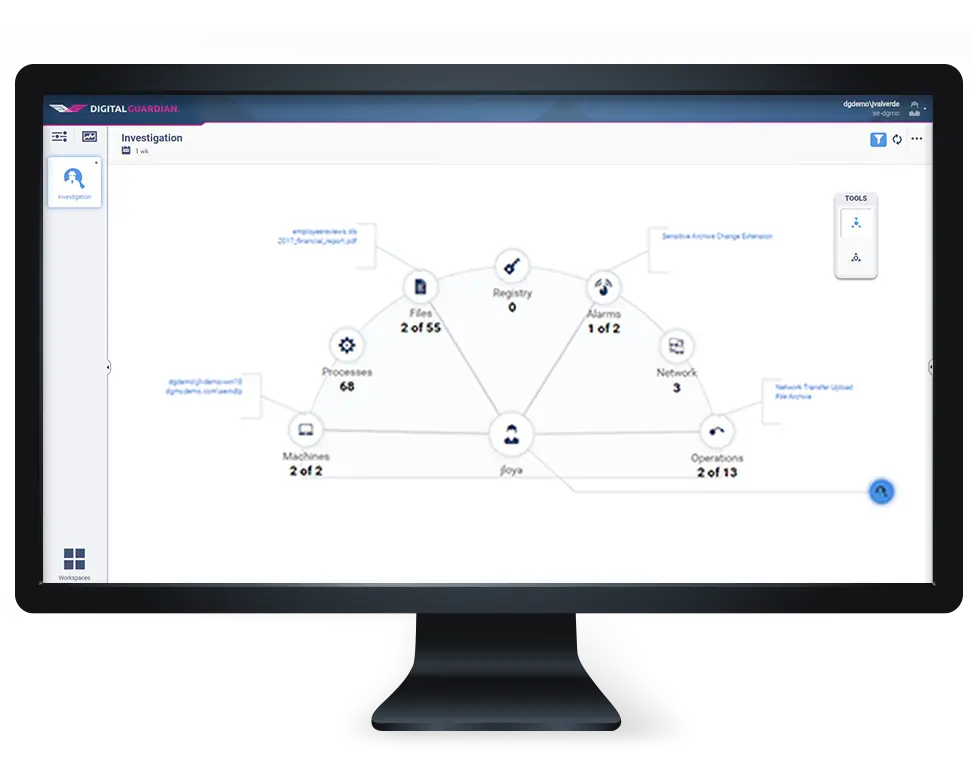
User Activity Monitoring Software - Identify and Mitigate Risky User Behavior
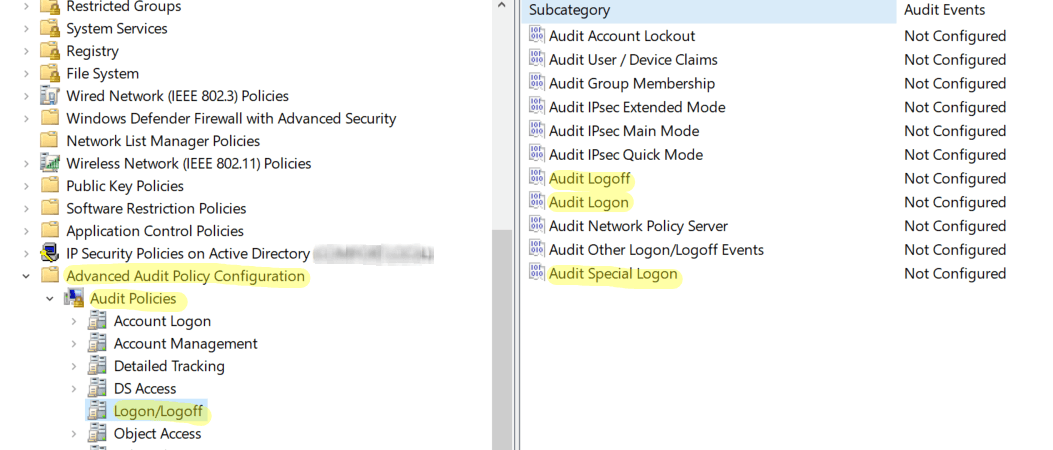
How to identify suspicious insider activity using Active Directory

Detect Potentially Suspicious Activity In Teams With Cloud App Security – Sam's Corner

Your IT Security and Access Control Checklist

Stop Stream Trolls On Twitch - Use Suspicious User Detection

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks
Hunting for Suspicious DNS Requests with Short Domain Extensions

The best passwordless authentication tools 2023 Authsignal
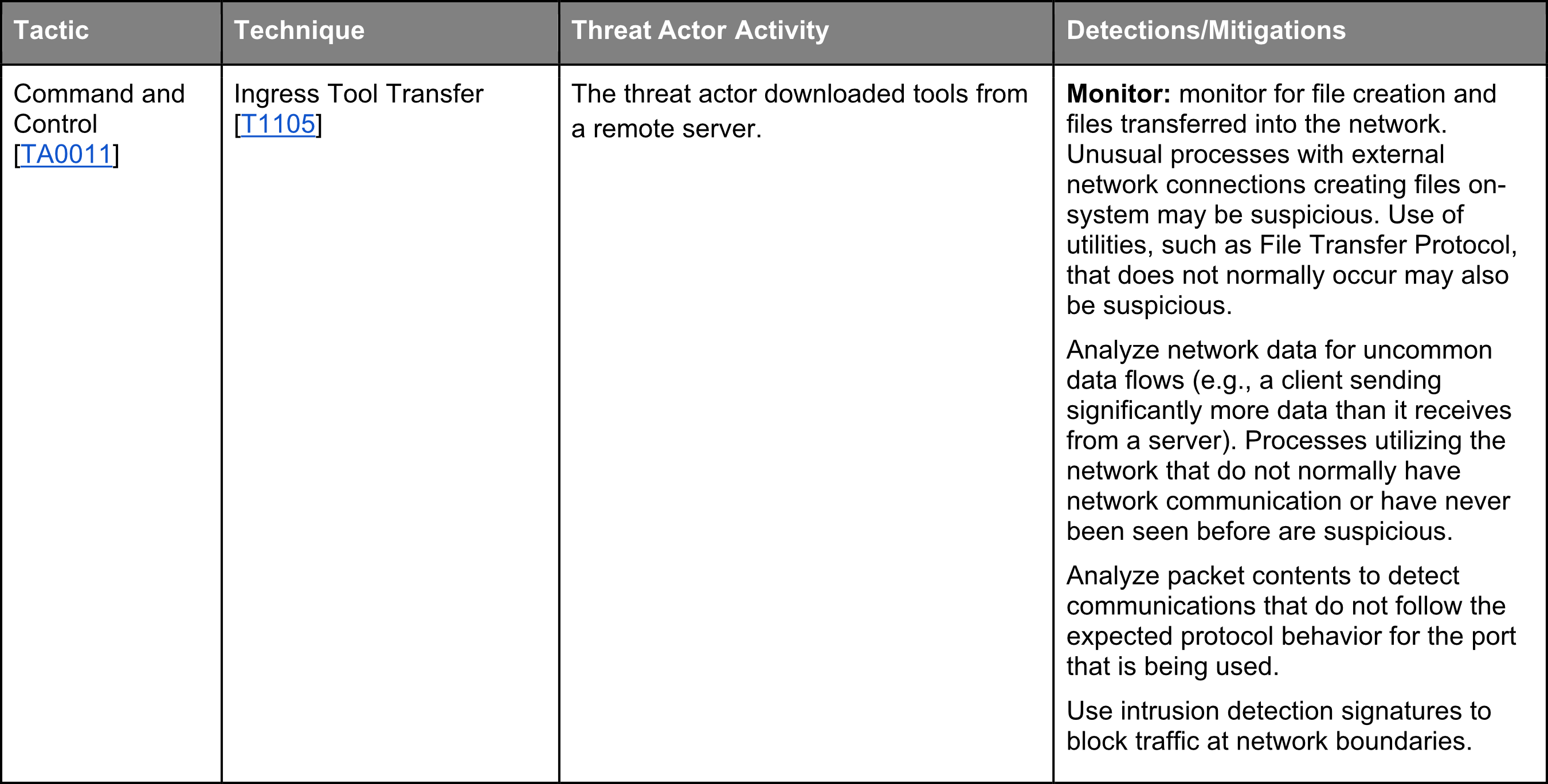
TRITON's Tactics and Techniques in the Enterprise domain + mitigations - Part 8 - SEQRED
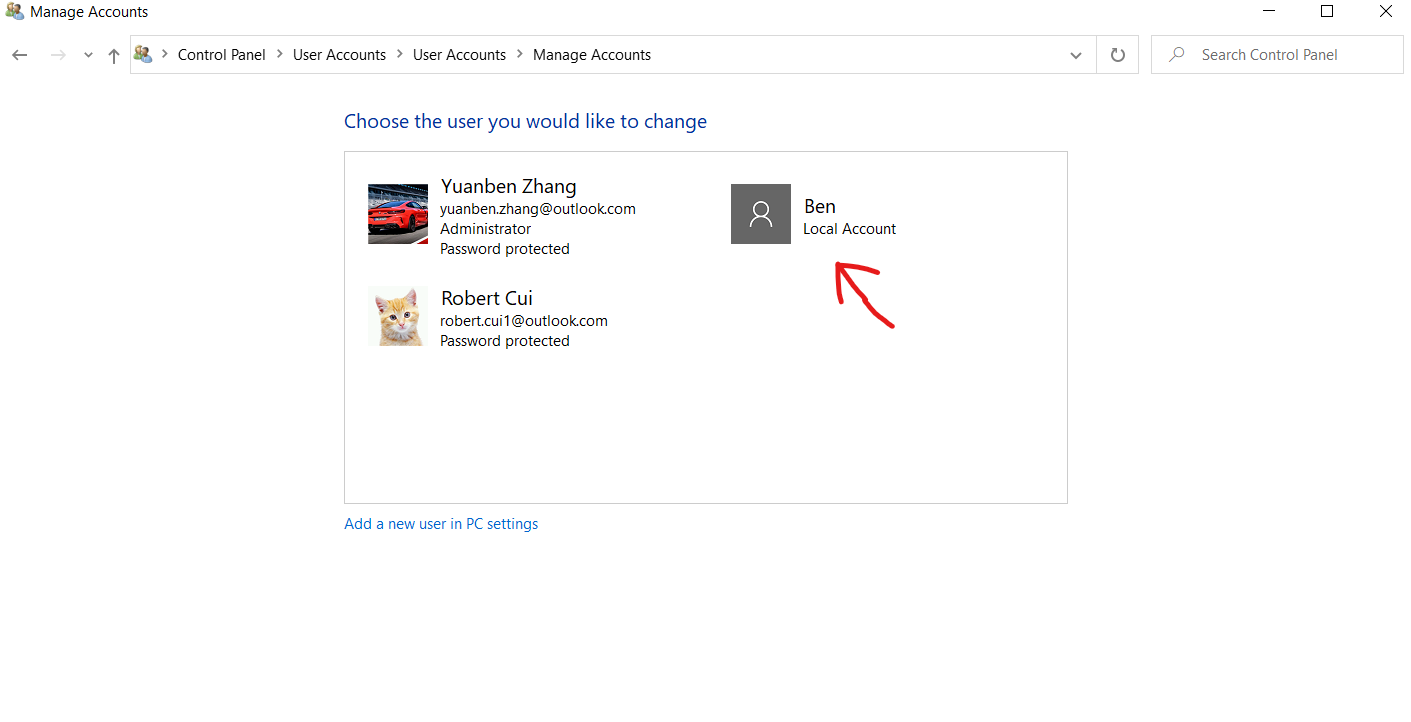
Found suspicious new user on my computer - Microsoft Community

RUMOR CONTROL: Users report suspicious text across Mobile, Baldwin counties
de
por adulto (o preço varia de acordo com o tamanho do grupo)





:quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/NE5TC5J5NVAAJEZ6PRPZRXNOVM.jpg)
