PDF) Valkyrie : Vulnerability Assessment Tool and Attack for Provably-Secure Logic Locking Techniques
Por um escritor misterioso
Descrição
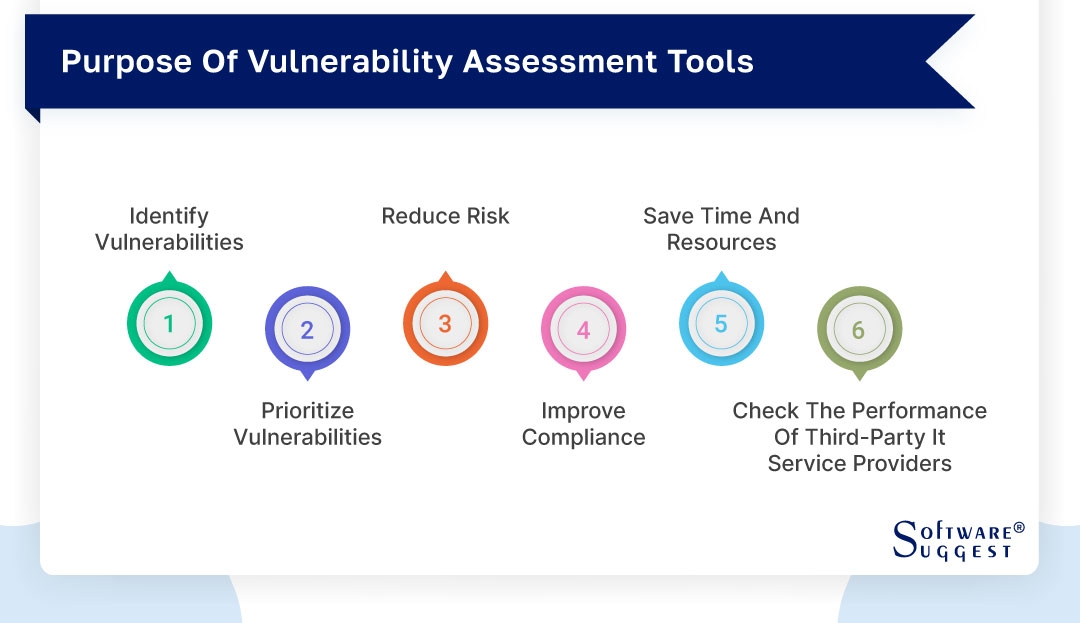
20 Best Vulnerability Assessment Tool in 2023

Cthulhu Hack - Valkyrie-9

PDF) ATPG-based cost-effective, secure logic locking

PDF) Embracing Graph Neural Networks for Hardware Security (Invited Paper)

PDF) Valkyrie : Vulnerability Assessment Tool and Attack for Provably-Secure Logic Locking Techniques

PDF) Provably-Secure Logic Locking: From Theory To Practice
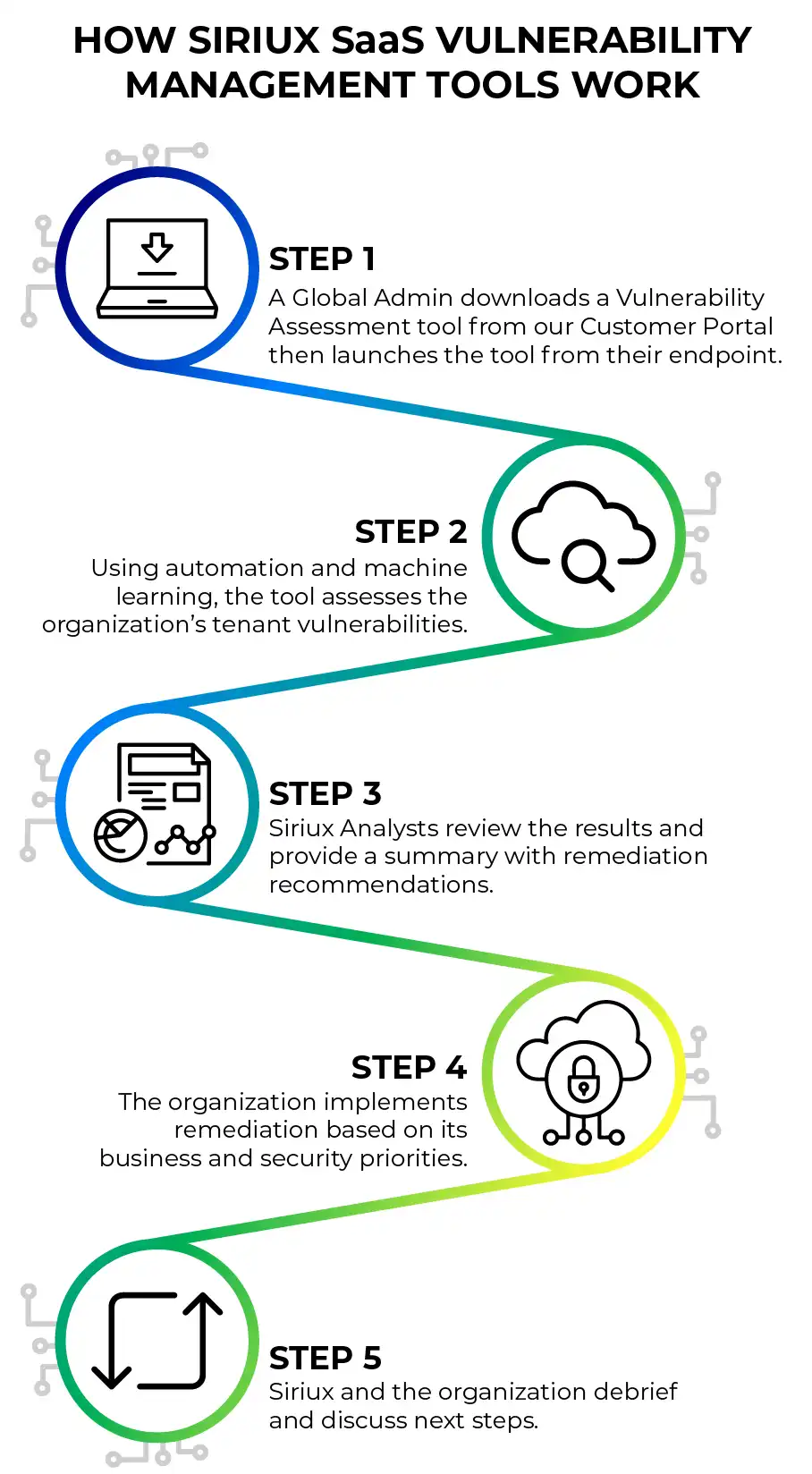
Siriux - Razorthorn Security
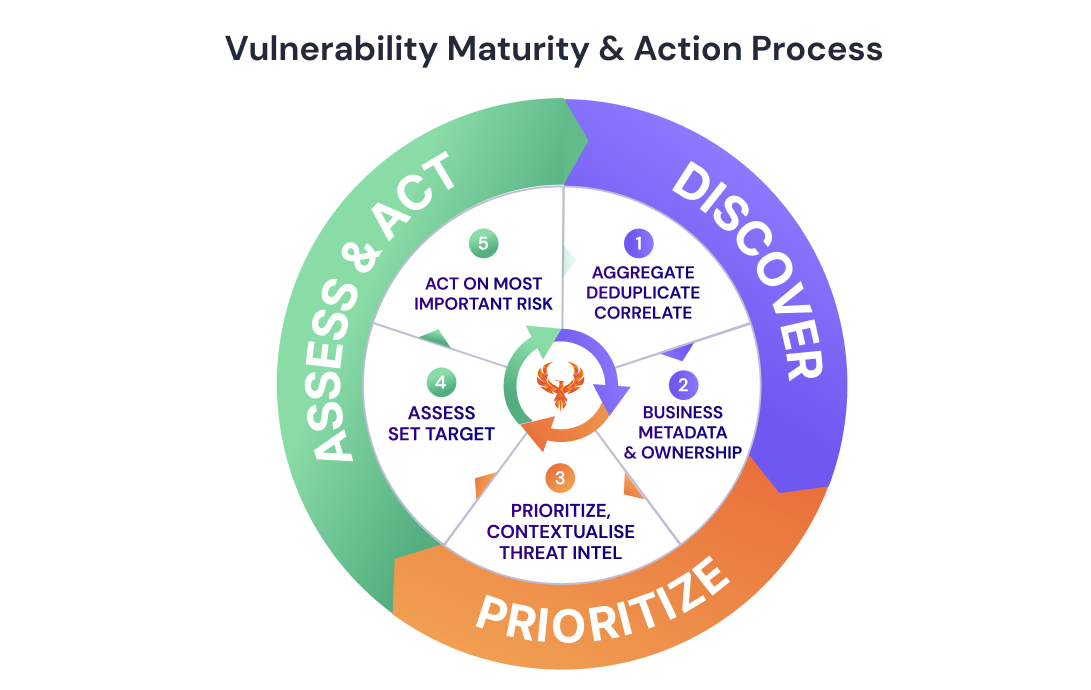
Vulnerability Managment Framework - Application Security - Code to Cloud

PDF) Logic Locking: A Survey of Proposed Methods and Evaluation Metrics
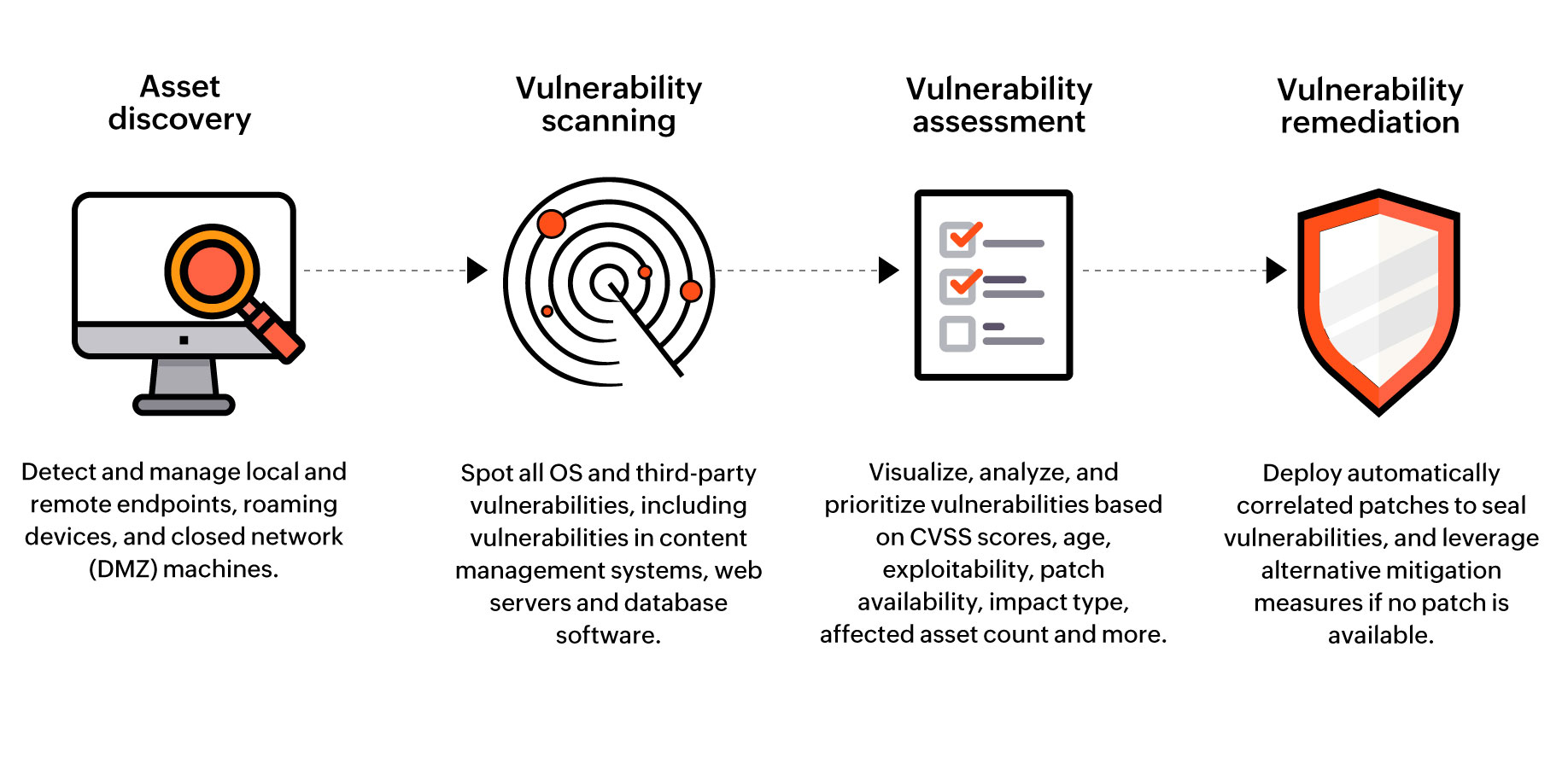
Vulnerability Diagnostic - Platform & Web Diagnostic

PDF) Logic Locking: A Survey of Proposed Methods and Evaluation Metrics

PDF) Embracing Graph Neural Networks for Hardware Security (Invited Paper)
de
por adulto (o preço varia de acordo com o tamanho do grupo)






