Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Certified Information Security And Ethical Hacker
Ethical Hacking - How to start

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS
How to Become an Ethical Hacker in 2024 — A Step-by-Step Guide, by Mustapha Aitigunaoun, Dec, 2023

DeFi Protocol Temple DAO Struck by $2.3M Exploit

Postman Hack The Box (HTB). Hello guys today Postman got retired by…, by Musyoka Ian

Killnet Claim They've Stolen Employee Data from Lockheed Martin

Hackers breached Greece's top-level domain registrar

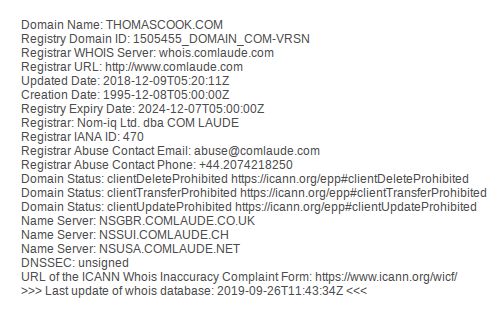
Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Ethical Hacking - Quick Guide

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
de
por adulto (o preço varia de acordo com o tamanho do grupo)