Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
Bypass malware detection in Google Play Store with Dynamic Code

Android: With Android 14, Google has a new plan to make your
Google blocks FOSS Android tool – for asking for donations • The
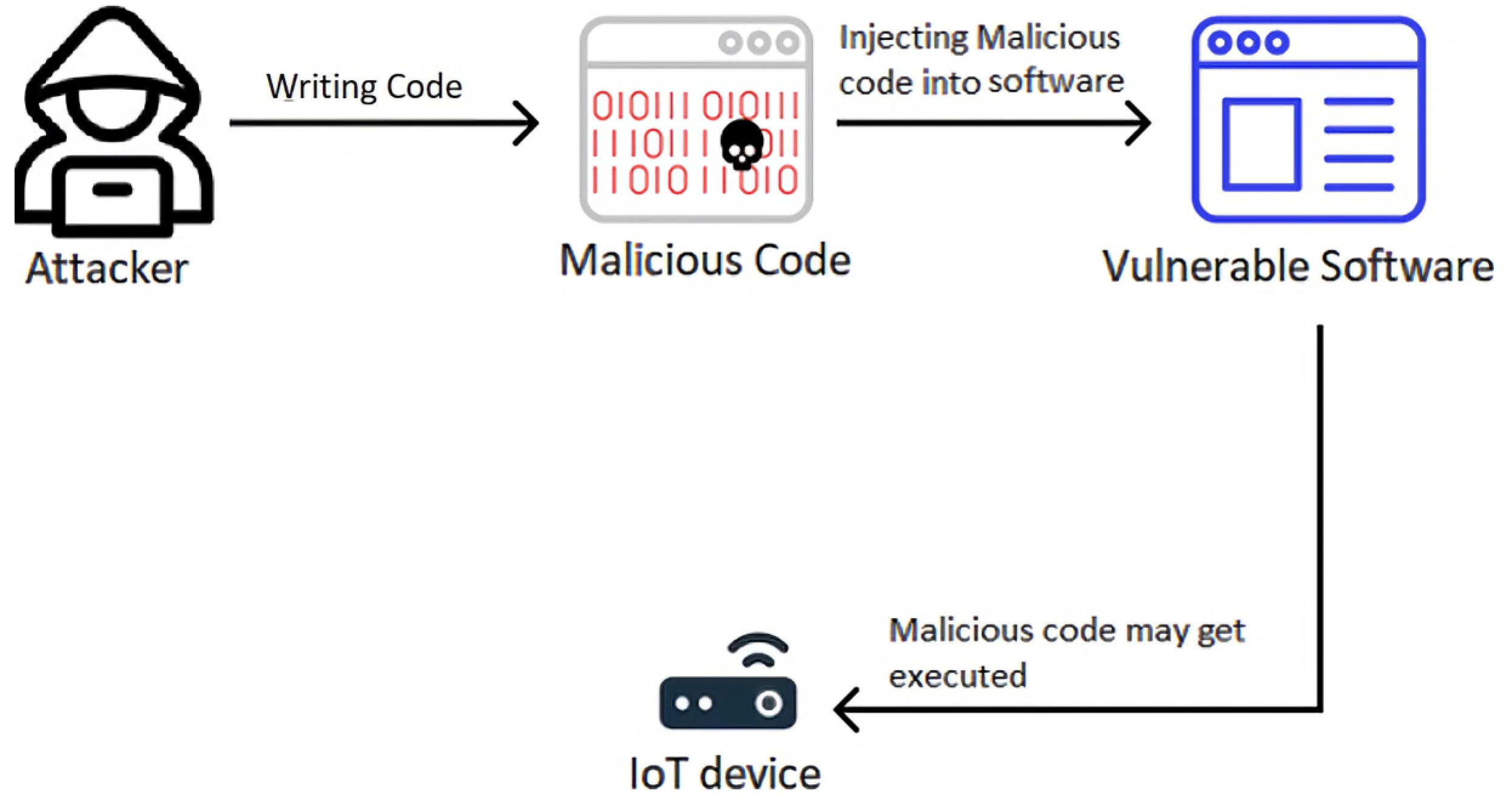
Sensors, Free Full-Text

SSL Pinning Bypass Android Using Frida

Tool Release: Magisk Module – Conscrypt Trust User Certs

One million Android users hacked by 'most sophisticated' attack

How to Code Sign Secured Android App with SHA Fingerprint Google
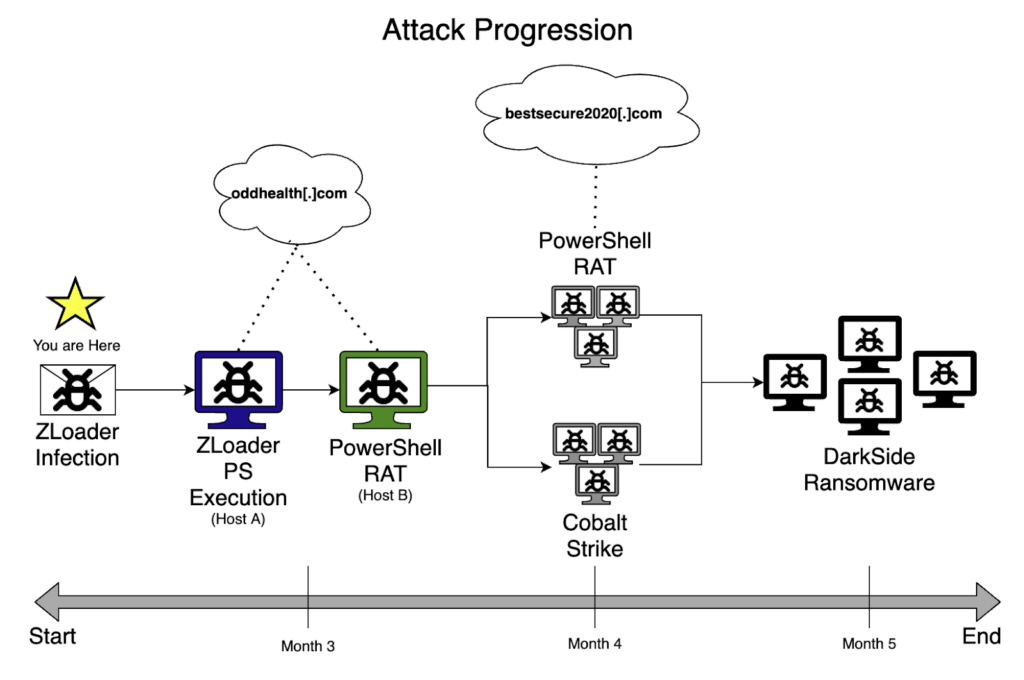
From ZLoader to DarkSide: A Ransomware Story

Objective-See

Load data using a third-party application, BigQuery

Analysis of dynamic code updating in Android with security
de
por adulto (o preço varia de acordo com o tamanho do grupo)







