Screen-shots of Part I and III of the user study. The usernames
Por um escritor misterioso
Descrição
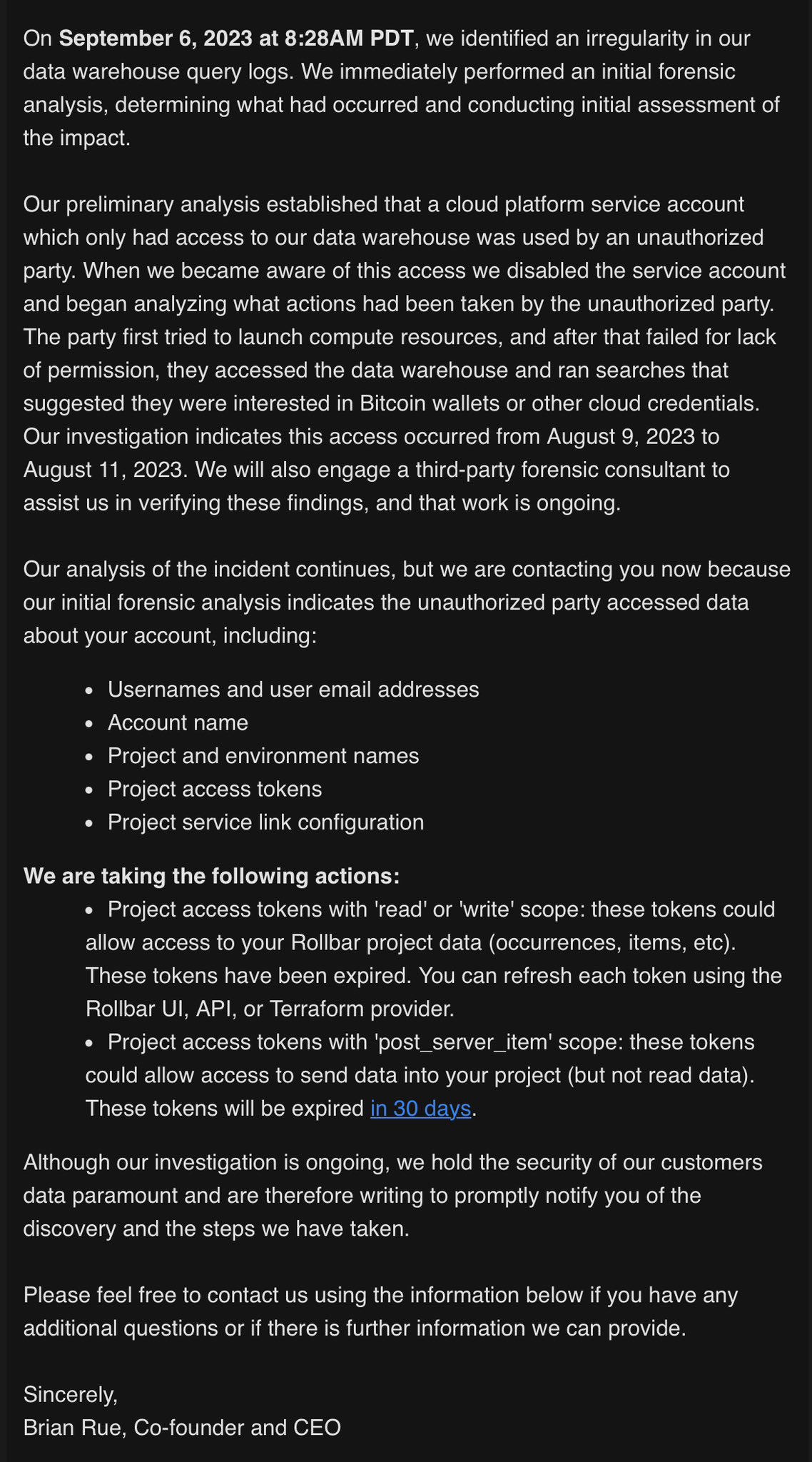
Troy Hunt on X: Data breach at @rollbar / X
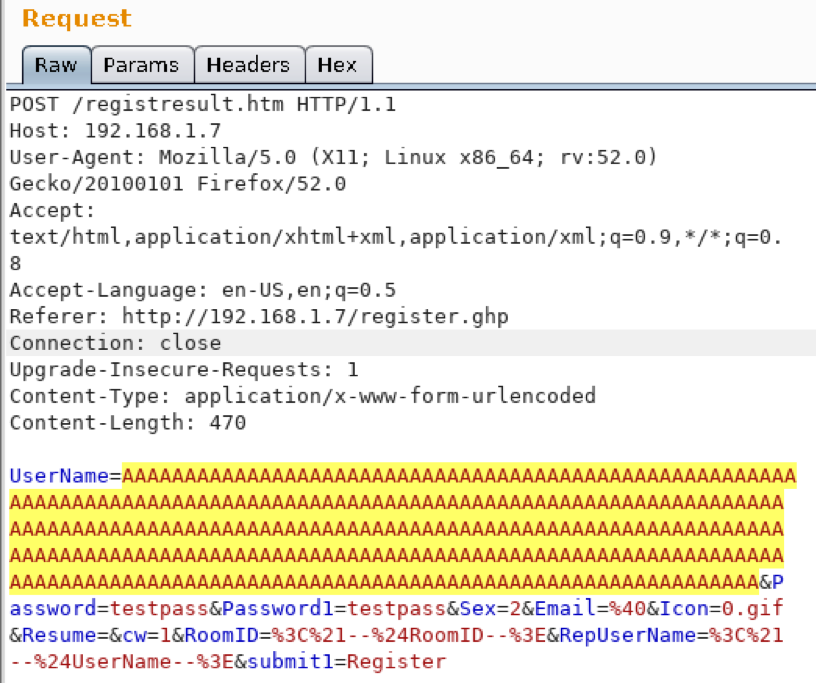
Exploit Development - Part 1: Python Exploit Development
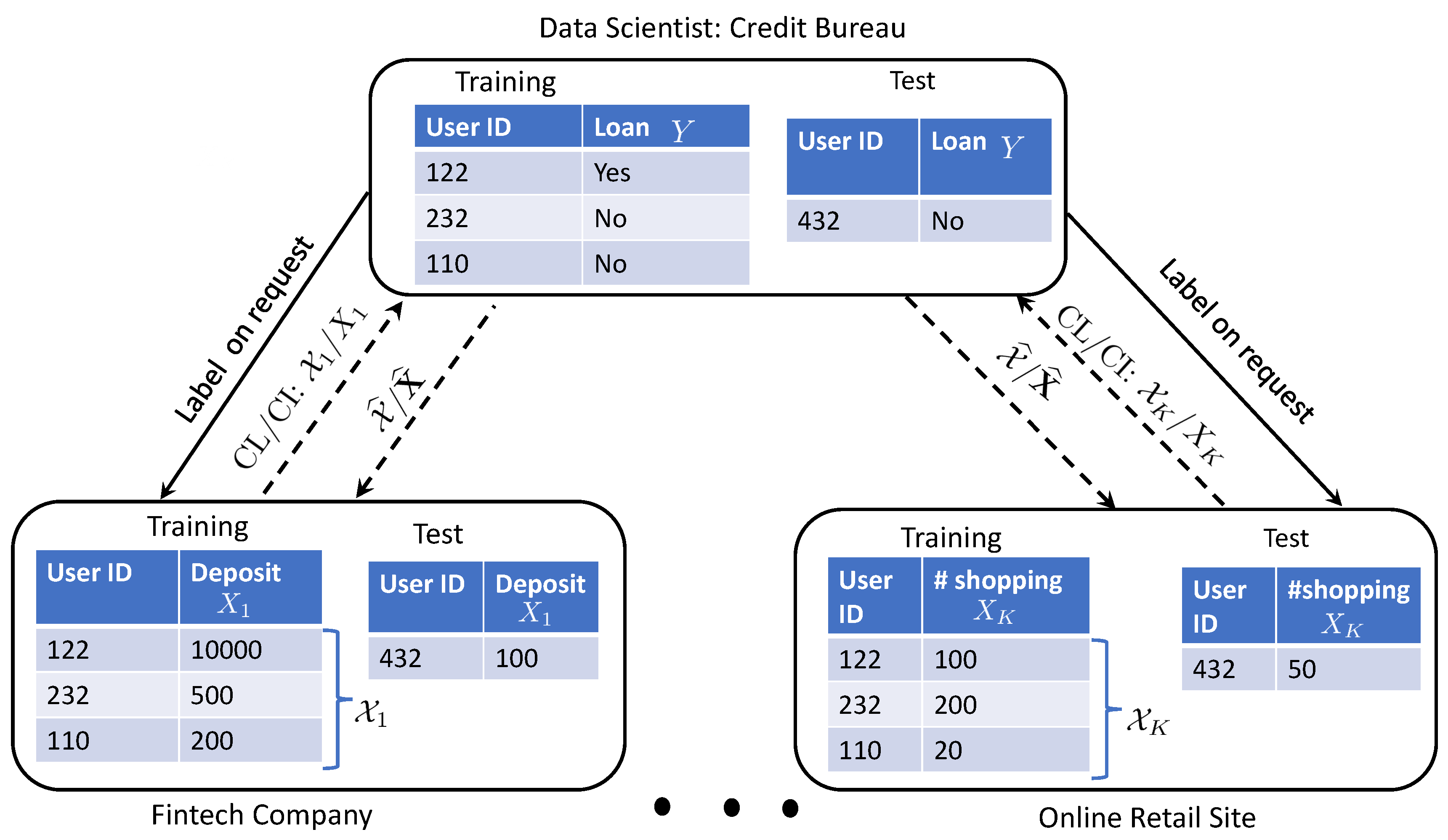
Entropy, Free Full-Text

Not able to edit Mapuser Names and unable to conne - Microsoft

Study Finds Healthcare Sector Uniquely Susceptible to Phishing

Medical Acupuncture
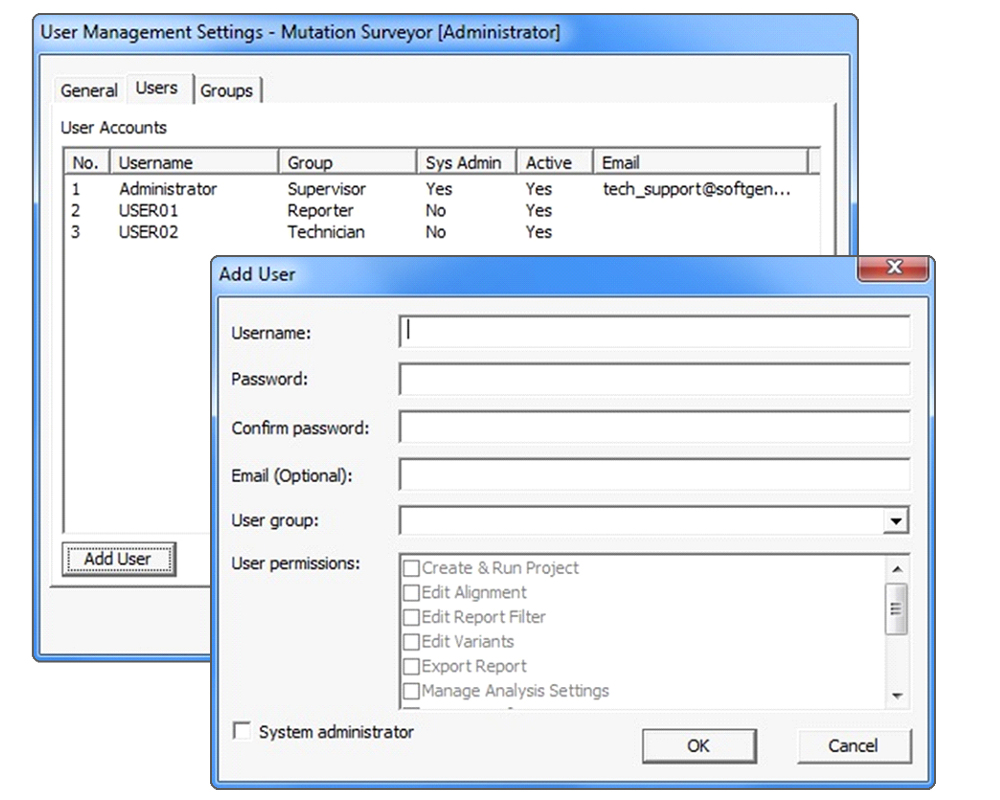
User Management

Professional development now just a click away

Women's Health Reports
de
por adulto (o preço varia de acordo com o tamanho do grupo)