Cybercriminals are shapeshifting to evade security controls
Por um escritor misterioso
Descrição

Human and technical ingenuity will be required to defeat shape-shifting malware

NIS 2: protecting against large-scale cyber incidents

InfraGard data for sale. Cyberespionage updates. Data sharing trends. Legitimately signed, but malicious

Nucleon Security

GenAI Cybersecurity: Where are we? Threats, Risks, and More
A survey on internet of energy security: related fields, challenges, threats and emerging technologies

Cyber Resolution for Intelligent Automation - EWSolutions
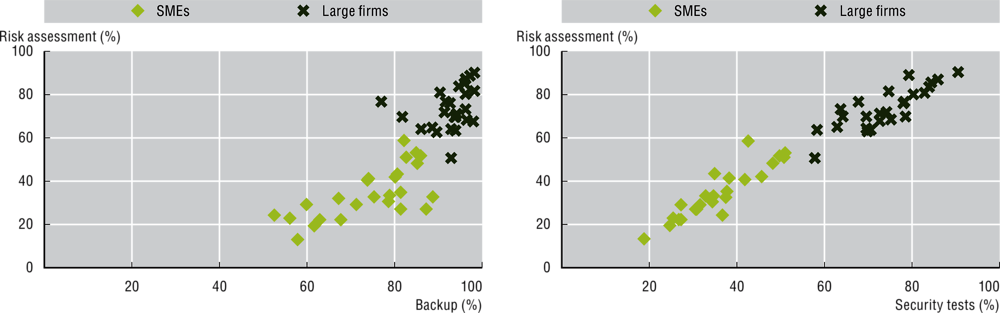
Chapter 7. Digital security, OECD Digital Economy Outlook 2020

Cyble — Aurora – A Stealer Using Shapeshifting Tactics

How Baiting Social Engineering Scams Target Organizations

What Are The Different Types of Computer Viruses?

Inside the FBI and DOJ Takedown of Qakbot, the “Swiss Army Knife” of Malware
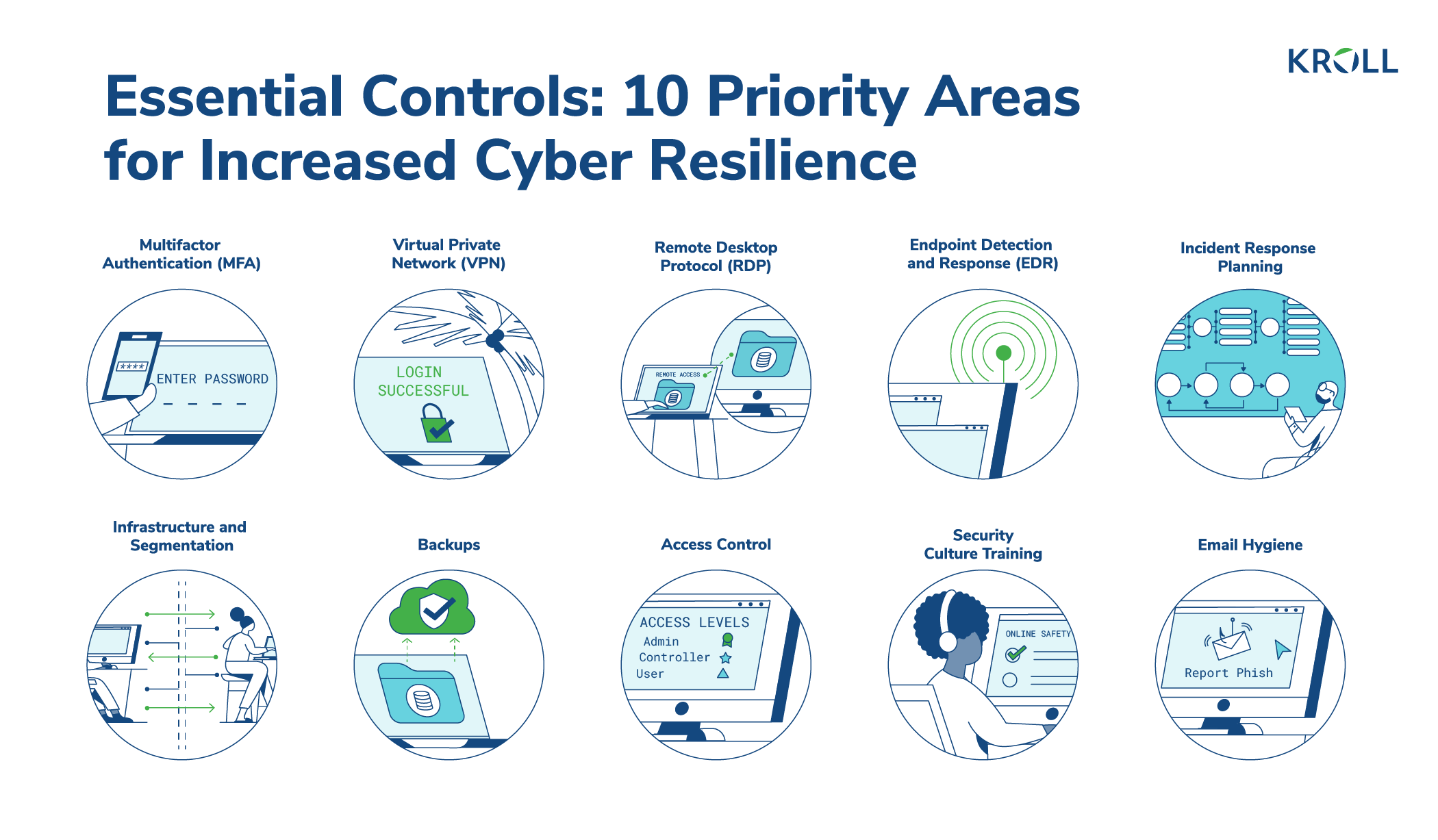
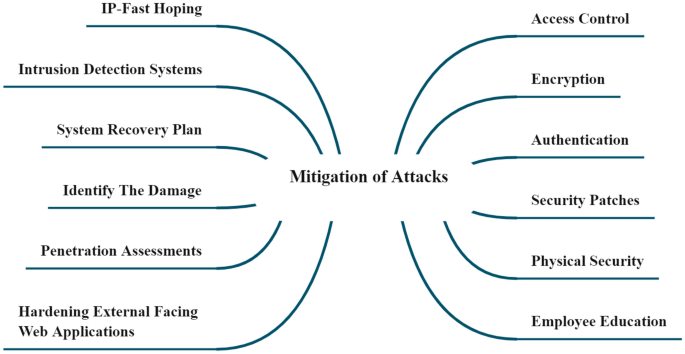
10 Essential Cyber Security Controls for Increased Resilience
de
por adulto (o preço varia de acordo com o tamanho do grupo)