window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
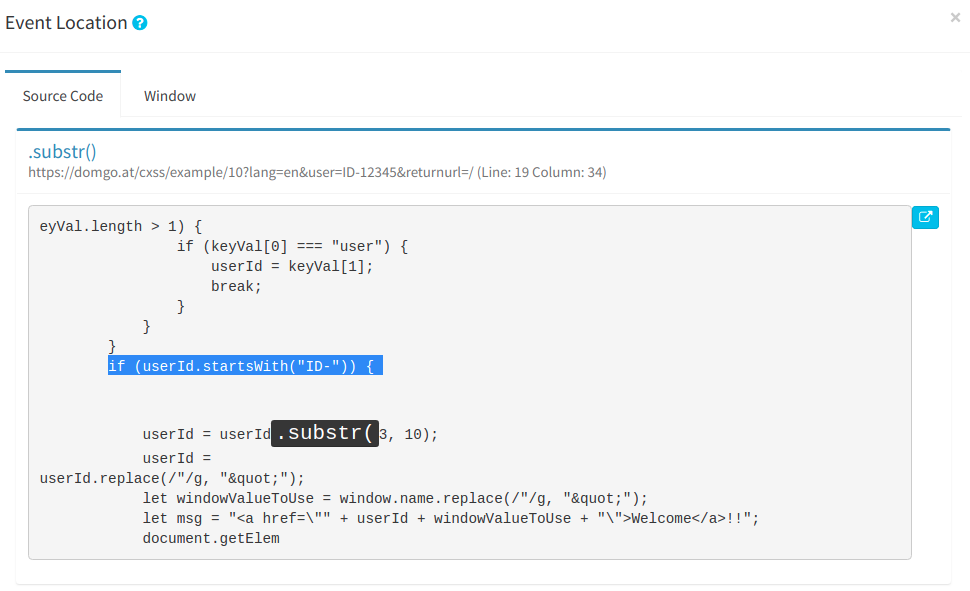
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
GitHub - s0md3v/AwesomeXSS: Awesome XSS stuff

Nextcloud 16 won't connect (No 'Authorization: Bearer' header found.) - Support - Joplin Forum
Node · GitHub

Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com, by Jonathan Bouman

java - Invalid port. Exiting..Exception in thread main org.openqa.selenium.WebDriverException: Driver server process died prematurely ChromeDriver Selenium - Stack Overflow
Missing required argument $name · Issue #294 · Smile-SA/elasticsuite · GitHub
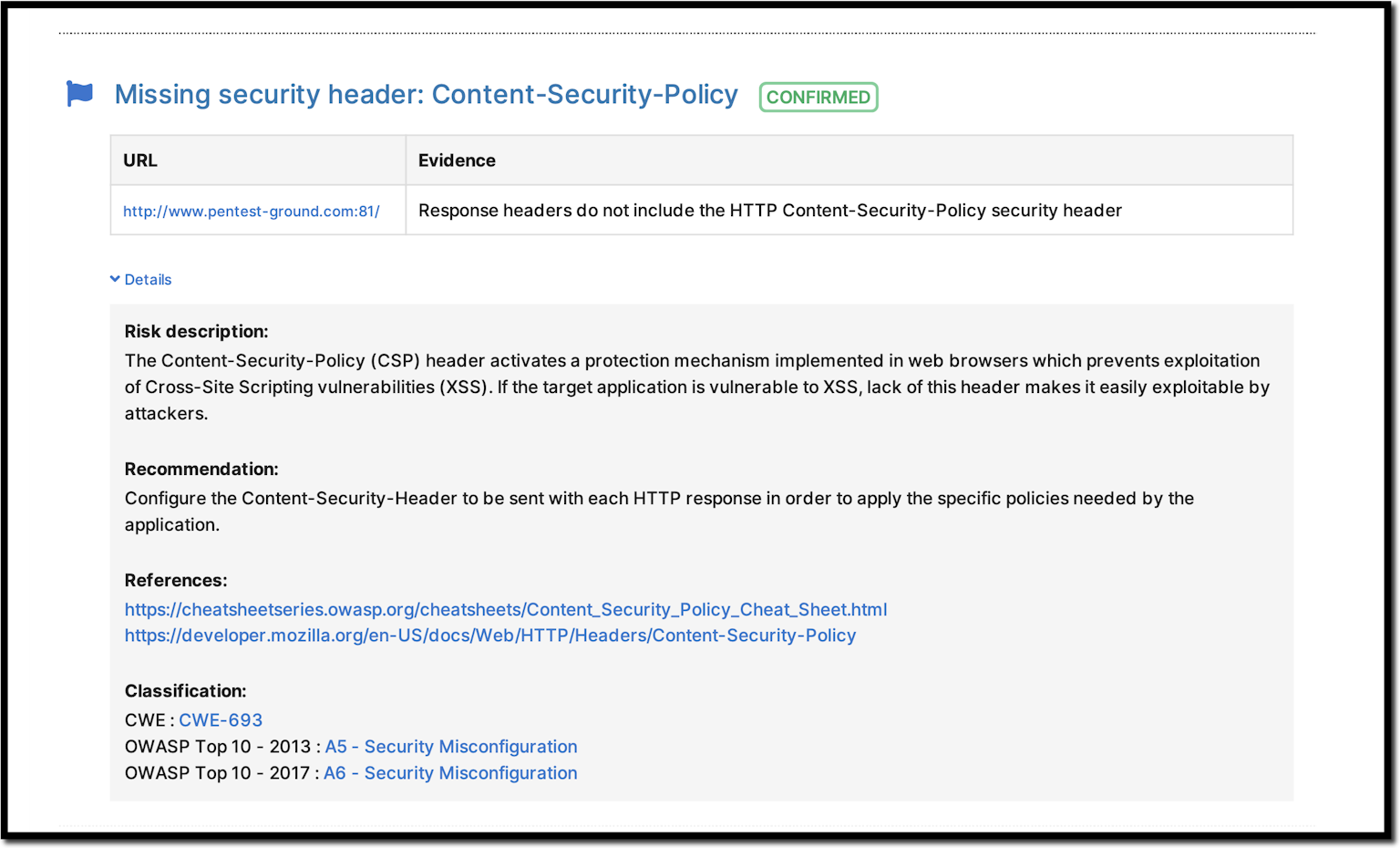
10 Practical scenarios for XSS attacks

Mutation XSS in Google Search
Basic Gist Account · GitHub
writeups/bug.md at main · tess-ss/writeups · GitHub

Cross-site scripting (Practice on PortSwigger) - HackMD

reactjs - WebStorm unable to recognise Next.js project - Stack Overflow
Development Board · GitHub

Mutation XSS in Google Search
de
por adulto (o preço varia de acordo com o tamanho do grupo)







