SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Descrição
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be

White Hat Hacker, Hacker design Pin by leo-jess
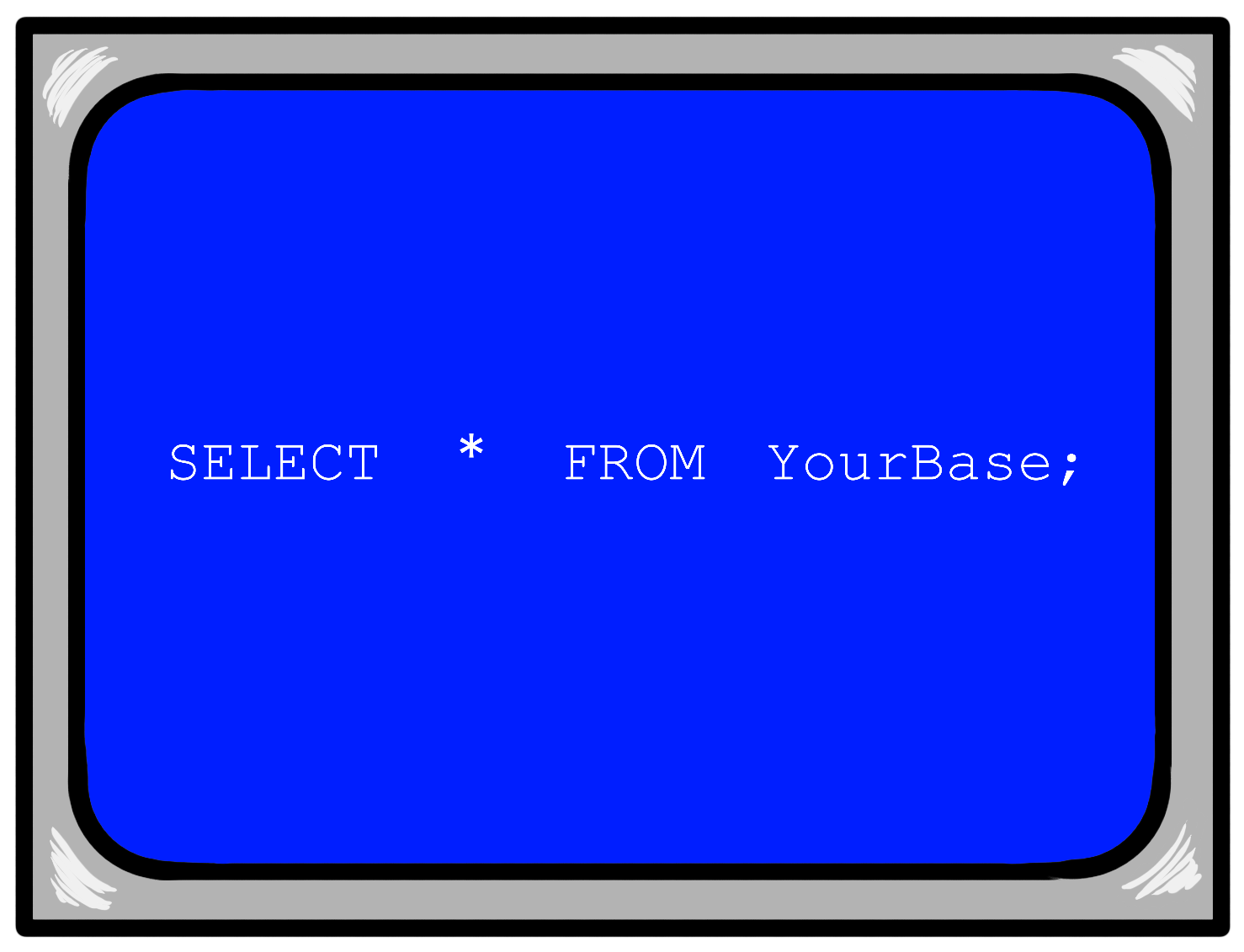
SQL injection and XSS: what white hat hackers know about trusting user input

Sql injections

PDF] Vulnerability Research and Mapping of Campus Network

PDF) Kosovo's websites vulnerabilities and its economic impact

What is SQL Injection ? Impact, Prevention and Remediation - TheHackerStuff
What is Stored XSS?. An introduction to stored cross-site…, by Vickie Li

Spidyhacker

Tool Release: Magisk Module – Conscrypt Trust User Certs, NCC Group Research Blog

What is Cross-site Scripting and How Can You Fix it?

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect

Four ways to combat the cybersecurity skills gap

XSS- an application security vulnerability
What Is Cross Site Scripting and How to Prevent It? A Complete Guide
What is Hacking?, Hacking Definition
de
por adulto (o preço varia de acordo com o tamanho do grupo)






